SSO Authentication with Okta
To provide easy and secure access to Action1 console, Action1 enables users to log in using single sign-on (SSO) instead of maintaining Action1-specific user credentials. This section explains how to configure SSO with Okta as an identity provider.
Stage 1: Configure Okta
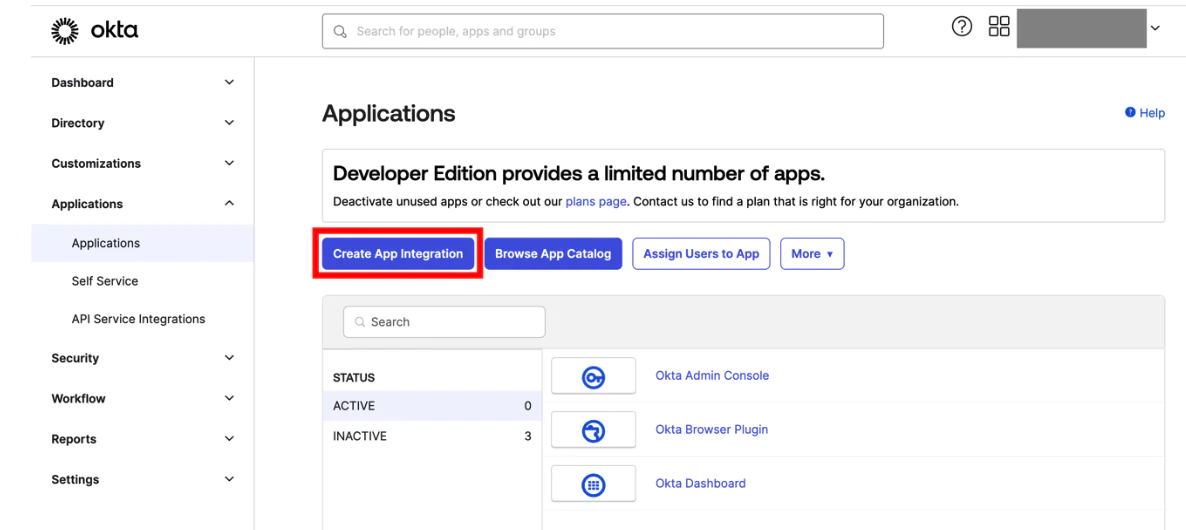
- Sign in to Okta console as administrator.
- Navigate to Applications and select Create App Integration.
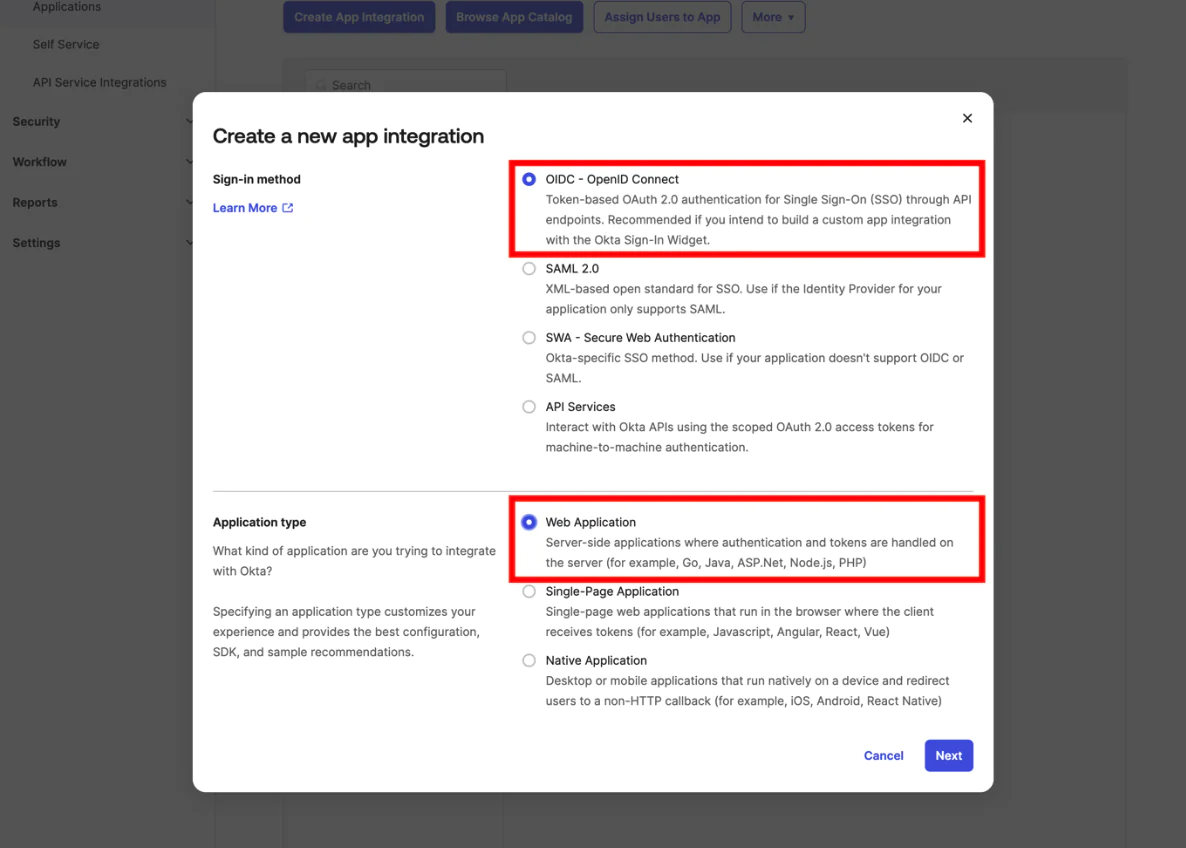
- Set the sign-in method to OIDC – Open ID Connect and the application type to Web Application.
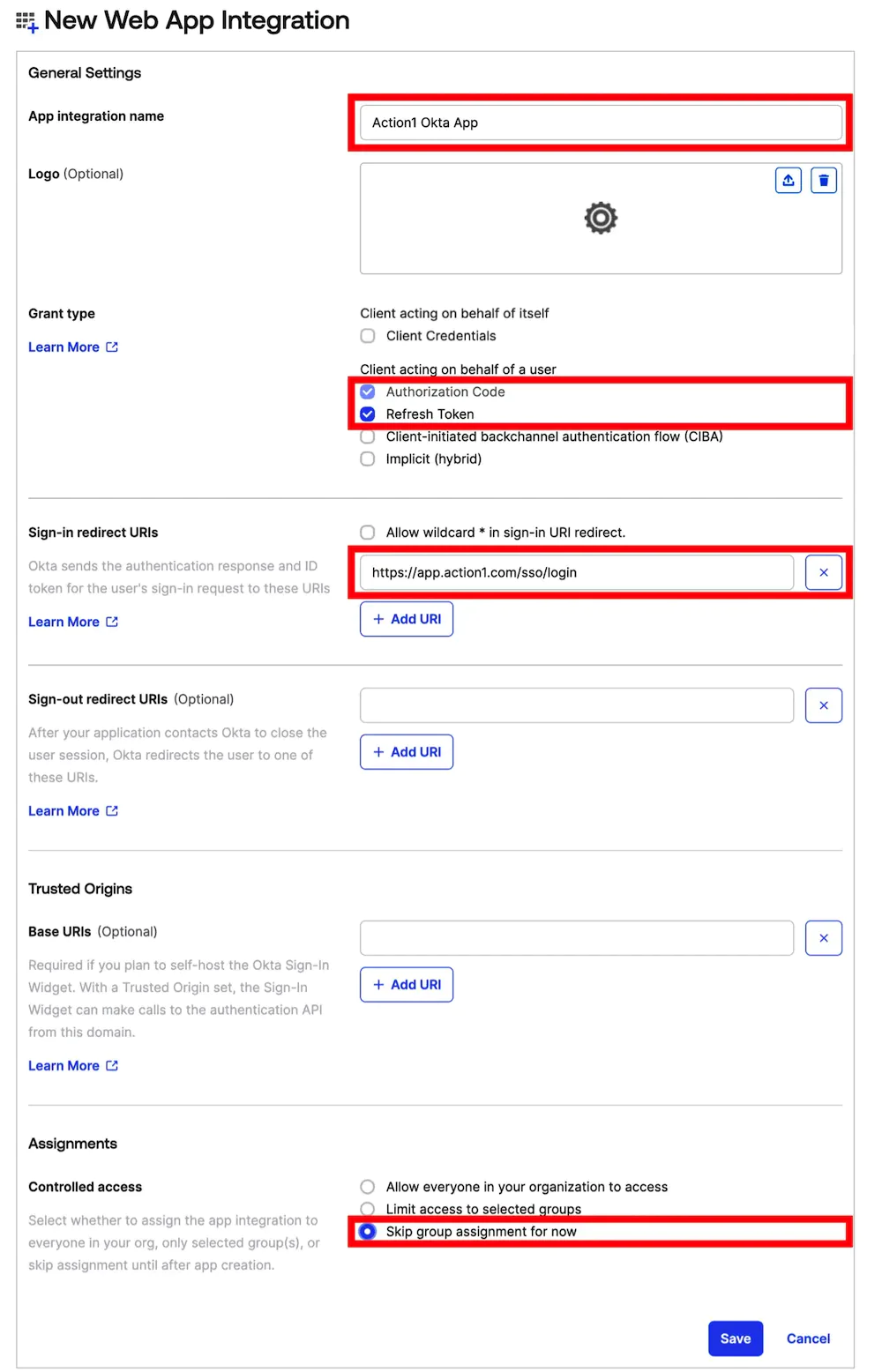
- Proceed to the app’s General settings and complete the following fields:
- Provide a name in the App integration name
- As a grant type, select Refresh Token. Authorization code is enabled by default.
- Depending on your region, set the Sign-in redirect URIs:
- North America: https://app.action1.com/sso/login
- Europe: https://app.eu.action1.com/sso/login
- Australia: https://app.au.action1.com/sso/login
- In Assignments, set Controlled access to Skip group assignment for now, and Save.
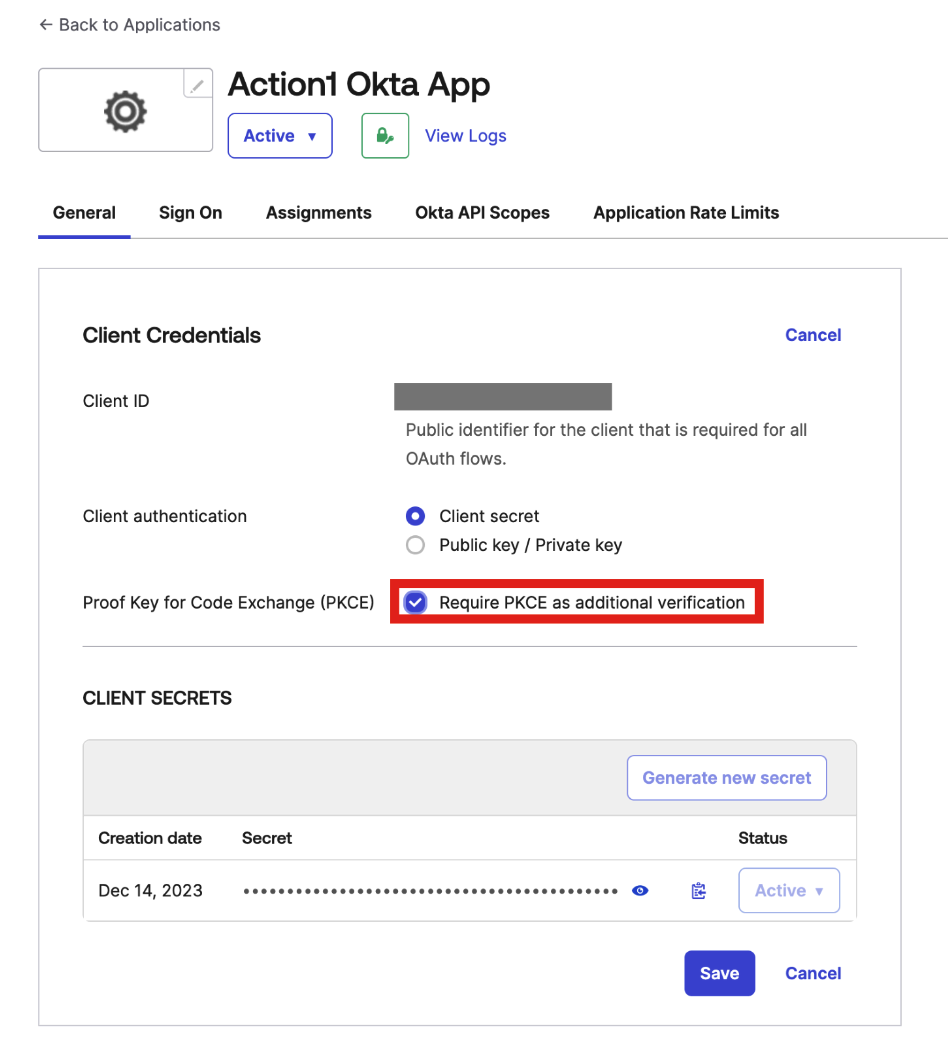
- Navigate to the app you created.
- On the General tab, select Require PKCE as additional verification.
- Copy Client ID and Secret to use later in Action1 settings.
- On the Assignments tab, specify users who can log in to Action1 using Okta integration. Note that users must be already created in Okta.
- Navigate to Security | API and copy Issuer URI to use later in Action1 settings. By default, the Issuer URI includes your Okta organization name (“https://${yourOktaOrg}”).
Stage 2: Enable SSO with Okta in Action1 Console
When you sign up for Action1, you have to create the initial Action1 credentials (without SSO). By default, this initial account has an Enterprise Admin role in Action1. Then you can use this privileged account to invite the existing accounts from your organization’s Okta.
After creating the initial Action1 credentials while signing up, follow these steps to enable Okta SSO:
- Log in to Action1 using your initial Action1 credentials (do not click Okta during login).
Important! Do not click Okta during this login.
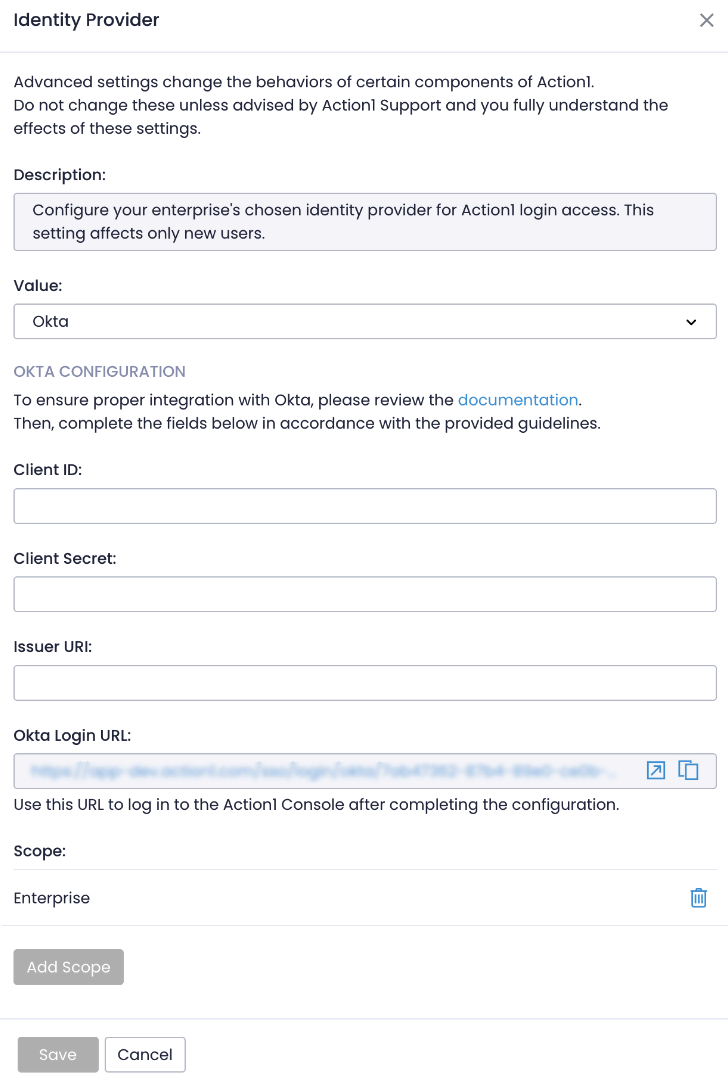
- Navigate to the Advanced page and select Identity Provider.
- Specify Okta as the identity provider. Keep the scope set to Enterprise. With this setting changed, all new Action1 users will use Okta to sign in.
- Enter Client ID, Client Secret, and Issuer URI of your Okta application (see steps 7-9 from Stage 1 above).
Important! Keep the initial non-SSO Action1 credentials for emergency recovery purposes, in case you lose access to Okta. Store these credentials securely, as they have Enterprise Admin access by default.
Stage 3: Invite Okta Users to Action1
- Make sure these users already exist in Okta. If not, proceed to Okta to create users.
- Navigate to the Users & API Credentials page and click +Invite.
- Provide the user settings in the dialog displayed, then click Invite. An invitation email will be sent to the user’s email address you provided.
Switching Existing Users to Okta SSO
This procedure explains how to switch your existing Action1 users to SSO with their Okta accounts.
Before you start, make sure these users already exist in Okta. Otherwise, proceed to Okta to create user accounts.
Important! To perform the required steps, an account with the Enterprise admin role in Action1 is required. Make sure you have at least one Enterprise admin present; otherwise, admin account access will be lost. You can also create a secondary Enterprise admin or elevate another user to the Enterprise admin role.
Important! To migrate to SSO with Okta, the Action1 user accounts need first to be deleted. The users will be unable to access Action1 until the process is completed.
- Navigate to the Users & API Credential page in the Action1 console.
- Locate the user account you want to switch to SSO with Okta. If this user has an Action1 role assigned, make sure to revoke this role.
- Select Delete. Alternatively, set the user’s email to non-existent, such as “[email protected]”.
- Invite the user again into Action1 by sending an invite link, as described in the “Stage 3: Invite Okta Users to Action1” section above.