PCI DSS Compliance Patch Management Software
For Securing Distributed Endpoints
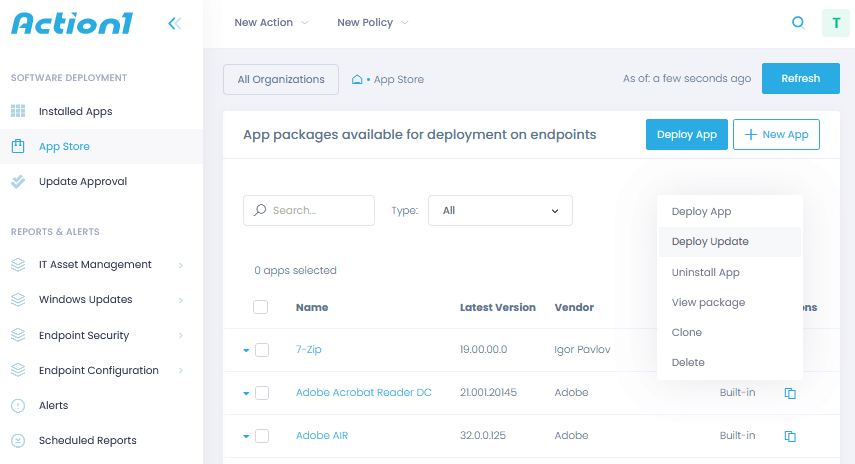
Patch Windows OS and third-party applications
Deploy approved software and remove unauthorized one
Onboard new devices with consistent security configurations
Inventory endpoint software and hardware
Maintain secure endpoint configurations
PCI DSS Requirements Action1 Helps With
Requirement 6.3: Identify and address security vulnerabilities
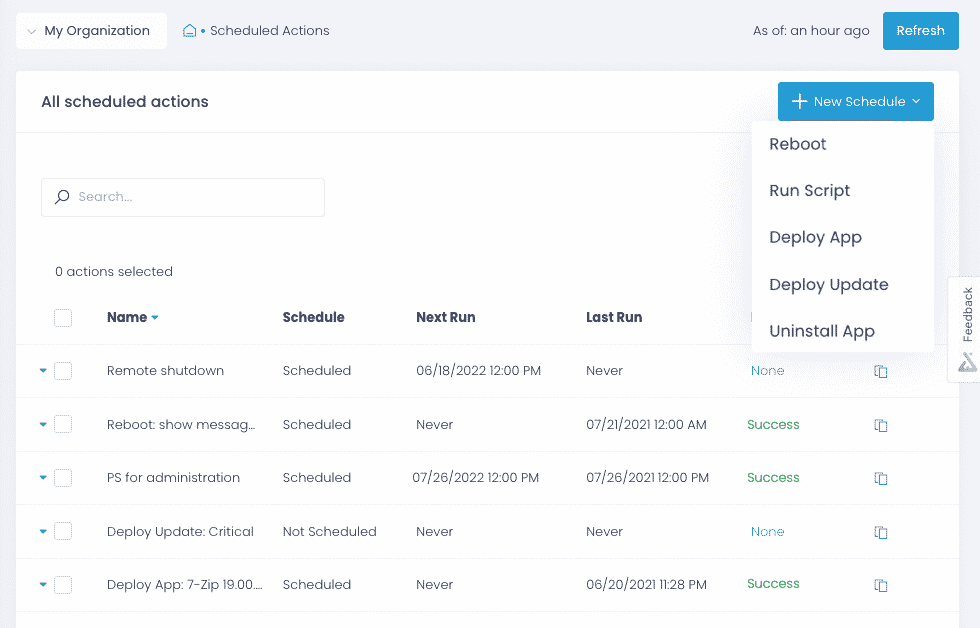
Automate patch management
Protect your systems and applications from known vulnerabilities by implementing a reliable and consistent patch management process. Patch all endpoints even if they are remote, not connected to a corporate VPN, not joined to a domain, or are offline.
Discover available updates
Never miss a critical or security patch. Identify what Windows OS and third-party application updates are available, but lacking on your endpoints, and be notified about new Windows updates.
Enforce patch management policy
Prioritize patches by their severity, approve updates for deployment manually or automatically and schedule updates granularly—all to ensure your critical systems and devices are patched ASAP.
Demonstrate compliance
Get ad-hoc and scheduled reports on installed updates to prove your PCI compliance to auditors. Verify patching results in real time and without the need to check every endpoint manually.
Requirements 5.2-5.3: Protect systems and networks from malicious software
Deploy and update anti-malware solutions
Ensure and prove to auditors that your endpoints are continuously protected with authorized and up-to-date anti-malware software by deploying it consistently across all onsite and remote endpoints and updating it as soon as a new update is released.
Deploy anti-malware solutions
Update anti-malware solutions
Update anti-malware software timely and consistently from a single location. Automatically patch applications, tested by Action1, or upload new versions of your custom applications for further testing and deployment.
Stay on top of security changes
Get real-time alerts on security events that can make your endpoints vulnerable to attacks and bring you out of PCI DSS compliance, such as the removal of an anti-malware solution from any endpoint.
Requirements 1.5, 2.2: Configure and manage system components securely
Automate endpoint configuration management
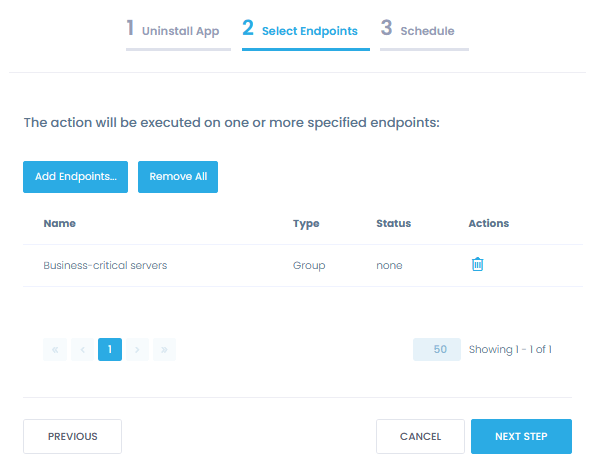
Apply consistent secure endpoint configurations across all endpoints, including new devices and employee-owned endpoints, that connect to both your cardholder data environment and untrusted networks.
Onboard new devices
Prevent insecure configurations from being introduced into the environment with a new device by applying your endpoint configuration standards to new devices automatically with multi-step policies.
Manage endpoint configurations
Ensure only necessary services and functions are enabled by running pre-built or custom scripts across any number of endpoints from a single console. Remove unnecessary software to minimize your attack surface.
Get alerts on configuration changes
Verify that your endpoint security controls are running with reports, and get real-time alerts when someone tampers with endpoint configurations, accidentally or intentionally.
Requirements 12.2-12.3: Identify and manage risks to the cardholder data environment
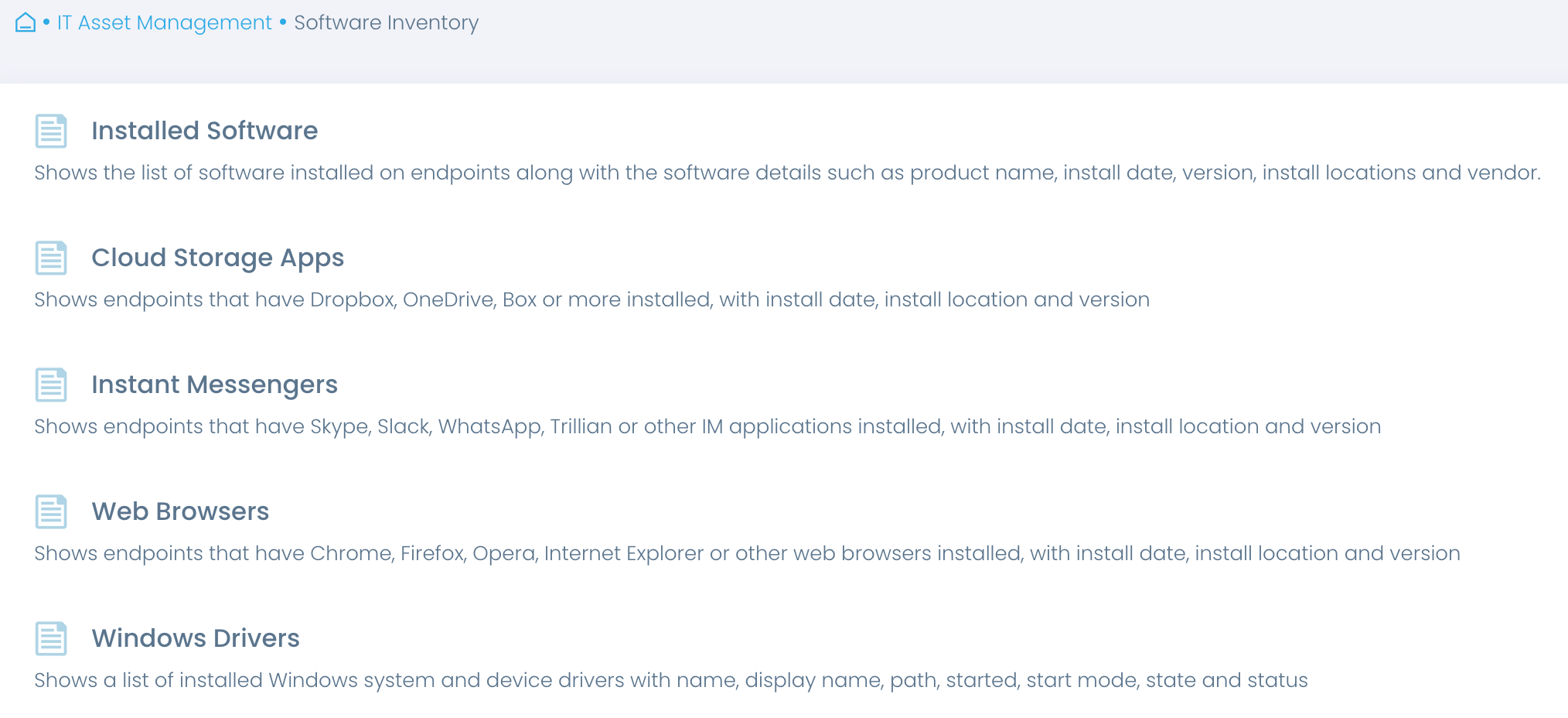
Maintain up-to-date asset inventory
Automate asset inventory and gain accurate real-time insights into software and hardware technologies business users rely on. Streamline regular reviews of software and hardware in use and verify that these components continue to be updated.
Review hardware assets
Get an overview of endpoint hardware to make informed decisions about required hardware replacements and upgrades and ensure hardware remains current, supported by the vendors, and compliant.
Enforce the use of approved software
Verify that no unauthorized software is installed on endpoints posing a risk to your environment and sensitive data. Find unauthorized or unsupported software and remove it to solidify your data security.
Detect asset changes
Stay on top of hardware and software changes, such as unauthorized software installation, antivirus deinstallation, or Bitlocker status changes, to respond to incidents quickly with real-time alerts.
Security Is Our Priority
Action1 not only helps organizations adhere to the PCI DSS standard on patch management and endpoint security configurations, but also is a secure solution itself, compliant with PCI DSS requirements for administrative access and inbound traffic to the cardholder data environment.
PCI security features
Action1 enforces two-factor authentication, provides role-based-access and audit logs, and secures all connections with TLS 1.2 and AES-256.
Compliant solution
Action1 is compliant with the requirements of security standards and regulations, such as SOC 2, ISO/IEC 27001, and NIST SP 800-171
Secure remote access
Action1 saves you from poking extra holes in your firewall configuration, such as opening an inbound port for remote connections to resources.
Trusted by thousands of IT teams around the world
10M+
Managed Endpoints
3,000+
Customers
99%
Patch success rate


Why customers choose Action1
Tame complexity
Get up and running and start getting value in one hour, with a solution that is easy to deploy and just works. No legacy technology and feature overload.
Do it all in one place
Patch business–critical systems and applications, deploy security software, configure endpoints and maintain asset inventory—all from a single centralized location.
Stay flexible
Implement patch management, endpoint security and monitoring requirements the way your organization needs, with granular, easily customizable policies.
Optimize workflows
Improve compliance rates and maximize efficiency by integrating Action1 with your existing risk management, log analysis and compliance software via a RESTful API.
See phenomenal ROI
Get support you deserve
If any issues arise with our PCI DSS compliance software, have them promptly and definitively resolved by our knowledgeable and responsive support.
What Our Customers Say
With our previous tool, we were under constant risk, as 20% of our network was not being patched with security updates because they were off-site or not joined to our company domain. Action1 addresses this security gap by enabling us to establish a robust patch management program that covers 100% of our devices.
We are audited for ISO 27001:2018, and patch management is one of the requirements. Thanks to Action1, we’ve set up patching policies that meet our organization’s needs. As a result, we update the whole infrastructure in minutes. We also leverage Action1 to monitor the state of our IT assets as required by ISO 27001:2018.
Frequently Asked Questions
What is PCI compliance?
PCI Data Security Standard (DSS) was developed to address the proliferation of payment card data breaches.
PCI compliance is enforced by the PCI Security Standards Council (PCI SSC), an independent body created by Visa, MasterCard, American Express, Discover, and JCB.
Is PCI compliance required?
Who does PCI DSS apply to?
PCI DSS applies to all businesses that store, process, or transmit credit card information electronically, regardless of their size or transaction volume.
How to get PCI compliance?
To become PCI certified, a business should:
- Identify their compliance level. This level depends on the size of the business and how many transactions they process.
- Meet the requirements set by PCI DSS.
- Depending on the compliance level, complete a self-assessment questionnaire (SAQ) or an annual Report on Compliance (ROC), which is an external audit performed by a Qualified Security Assessor (QSA).
- Complete a formal attestation of compliance (AOC).
- Perform a scan of the network used to process payments. This scan is completed by an Approved Scanning Vendor (ASV).
- Submit the documents, such as SAQ, AOC, and an ASV scan report to their acquirer bank.
How much does PCI compliance cost?
The cost of PCI compliance depends on the company’s size and whether a not it qualifies for the Self-Assessment Questionnaire (SAQ). In 2022, to complete a Report on Compliance (RoC), an enterprise processing millions of payments per year can expect to spend $50,000-200,000 on average, while a small enterprise conducting an SAQ will spend $20,000 or less.
In case of non-compliance, any vendor or service provider who violates the PCI DSS may be subject to a penalty, which might be $5,000 to $100,000 monthly until compliance violations are fixed. The merchant’s ability to handle card payments may be suspended too.
What are the benefits of PCI compliance software?
In addition to saving a great deal of time and effort by automating the fulfillment of specific requirements, such as patch management, security configuration management, logging, and reporting, it minimizes the risk of missing something that could compromise cardholder data security. With PCI compliance software, organizations can achieve greater security, higher efficiency, speedier audits, and higher compliance rates.
What is PCI DSS Compliant Patch Management Software?
PCI DSS (Payment Card Industry Data Security Standard) Compliant Patch Management Software is a specialized tool designed to help organizations secure their systems by ensuring that all software and hardware are regularly updated with the latest security patches. PCI DSS, established by major credit card companies, sets specific standards that must be followed to protect cardholder data from breaches and fraud. One of the key requirements of PCI DSS is to maintain secure systems by applying security patches in a timely manner.
Patch management software automates the detection, testing, and deployment of patches across various systems, such as operating systems, payment processing software, point-of-sale systems, and other components that handle payment card data. The goal is to prevent security vulnerabilities that could be exploited by hackers to gain unauthorized access to sensitive financial information.
To comply with PCI DSS, organizations must ensure that all security patches, especially those addressing critical vulnerabilities, are applied promptly. PCI DSS Compliant Patch Management Software not only facilitates the patching process but also provides reporting and audit capabilities to prove compliance with PCI DSS standards. This helps organizations minimize the risk of data breaches and avoid costly fines or penalties associated with non-compliance.
Why is Patch Management Critical for PCI DSS Compliance?
Patch management is crucial for PCI DSS compliance because it directly impacts the security of systems that process, store, or transmit payment card information. PCI DSS Requirement 6.2 specifically mandates that organizations must establish a process to identify and apply security patches in a timely manner, particularly for critical vulnerabilities that could expose systems to unauthorized access.
Unpatched systems are one of the most common entry points for cybercriminals, as outdated software often contains vulnerabilities that hackers can exploit. A single unpatched vulnerability in a system that handles payment card data can lead to a serious data breach, exposing sensitive financial information and resulting in significant financial and reputational damage. In addition to data breaches, non-compliance with PCI DSS can result in hefty fines, increased transaction fees, and even the loss of the ability to process payment cards.
PCI DSS Compliant Patch Management Software automates the patching process, ensuring that all systems are consistently updated with the latest security fixes. This software also helps organizations maintain an audit trail of patching activities, which is essential for demonstrating compliance during PCI DSS audits. Proper patch management not only keeps your systems secure but also helps maintain the trust of customers and business partners by ensuring the protection of their sensitive financial information.
How Does PCI DSS Compliant Patch Management Software Improve Security?
PCI DSS Compliant Patch Management Software improves security by automating the process of identifying, deploying, and monitoring patches across an organization’s network. This is particularly important in environments where payment card information is processed, as hackers are constantly seeking vulnerabilities in systems that handle sensitive financial data. By keeping systems updated with the latest patches, this software significantly reduces the attack surface that cybercriminals can exploit.
Cyber threats, such as malware, ransomware, and data breaches, are often the result of unpatched software vulnerabilities. In the context of PCI DSS, a breach of payment card information can be devastating, both financially and reputationally. This software ensures that vulnerabilities are patched promptly and uniformly across all systems, including servers, databases, point-of-sale systems, and payment processing applications. It also offers centralized management, meaning IT administrators can oversee the patching process across the entire organization from a single dashboard.
Additionally, PCI DSS Compliant Patch Management Software provides comprehensive reporting and logging features. These features are crucial for compliance, as PCI DSS requires organizations to maintain detailed records of security measures. The software generates reports that show which patches have been applied, to which systems, and when they were deployed. This makes it easier to demonstrate compliance during PCI DSS audits and to quickly respond to security incidents.
In summary, by automating and streamlining the patching process, this software reduces the risk of cyberattacks and helps organizations stay compliant with PCI DSS, ensuring the safety of payment card data.
What Features Should You Look for in PCI DSS Compliant Patch Management Software?
When selecting PCI DSS Compliant Patch Management Software, there are several key features you should prioritize to ensure your organization maintains compliance and secures payment card data effectively.
First, the software should have robust vulnerability scanning capabilities. PCI DSS compliance requires organizations to identify security vulnerabilities and prioritize patching based on risk. Your patch management solution should automatically scan systems for vulnerabilities and provide real-time notifications when patches are available, especially for critical vulnerabilities that could impact payment card data security.
Automation is another essential feature. PCI DSS mandates timely patching of vulnerabilities, and manual patching can be time-consuming and error-prone. Automated patch management software ensures that patches are deployed quickly and consistently across all systems, reducing the likelihood of a breach caused by human error or delays in applying patches.
Detailed audit logs and reporting features are critical for PCI DSS compliance. The software should track every patching activity, including when patches were applied, which systems were updated, and who authorized the changes. These logs must be available for audits and security assessments, as PCI DSS requires organizations to document their security practices and demonstrate compliance during inspections.
Additionally, your software should support a wide range of platforms, including operating systems, payment processing software, and third-party applications. It’s crucial that all systems within the payment card environment are consistently patched, as even one vulnerable system can expose your entire network to risk.
Lastly, the software should provide role-based access controls, ensuring that only authorized personnel can deploy or approve patches. This aligns with PCI DSS’s requirements for limiting access to sensitive systems and ensuring that patch management activities are properly monitored and authorized.
By choosing software with these features, your organization will be better equipped to manage vulnerabilities, meet PCI DSS requirements, and protect payment card data from cyber threats.