Remediate Vulnerabilities
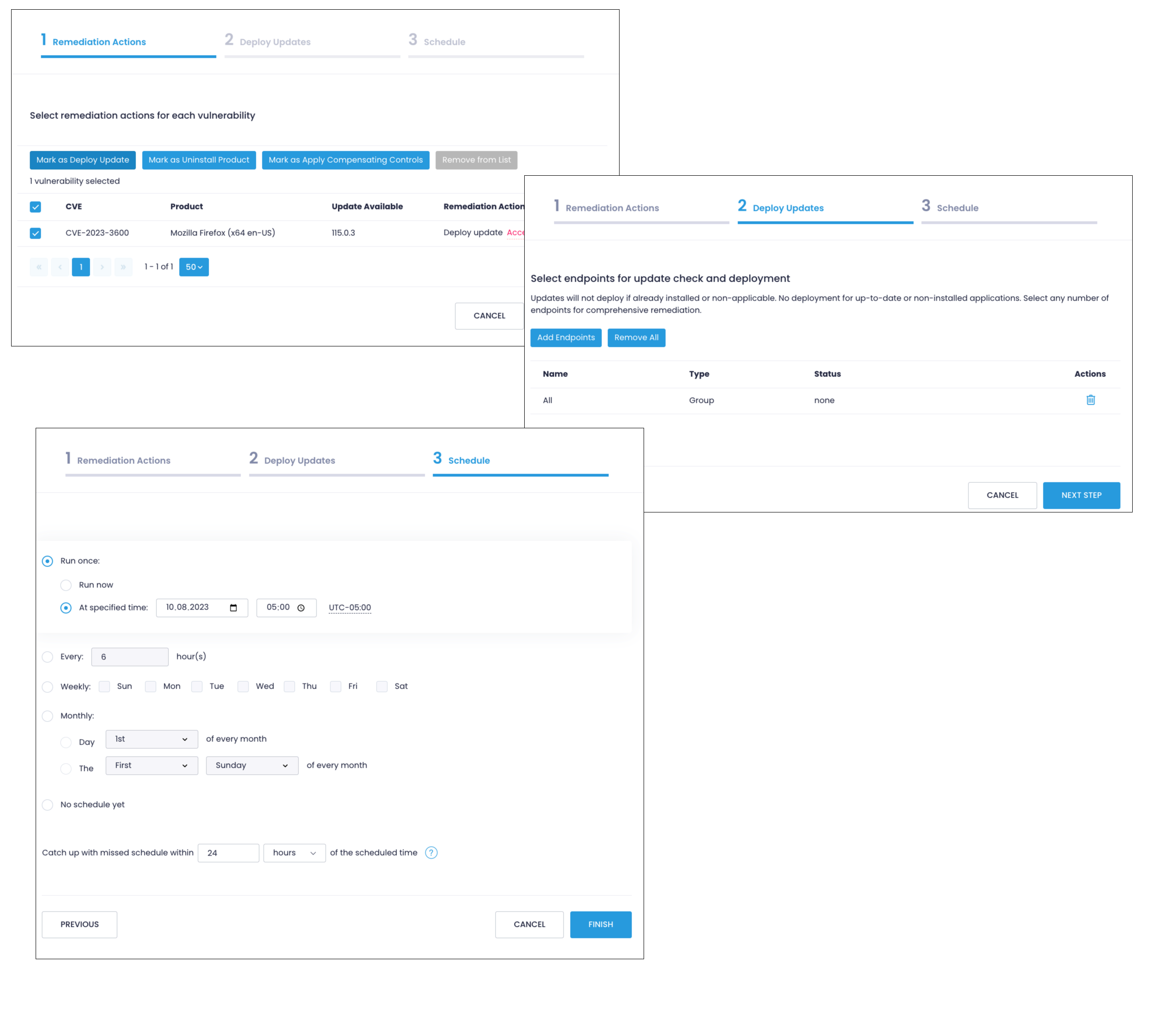
Action1 streamlines vulnerability management by allowing you to address detected issues across multiple endpoints at the same time. After reviewing security issues on the Vulnerabilities view, specify one or several CVEs from the list and select Start Remediation. Depending on the security issue, Action1 suggests one of the following remediation strategies: installing updates, uninstalling an app entirely, or applying compensating controls. If you remediate several CVEs at the same time, you will specify an action per CVE or product (CVEs for the same product will be grouped).
Option 1: Remediation by Installing an Update
Suggested option in case there is a new version of the app addressing the issue. Select Start Remediation and check selected CVEs, then choose Mark as Deploy Update. You might need to accept the EULA. In the next step, specify endpoints, then schedule execution.
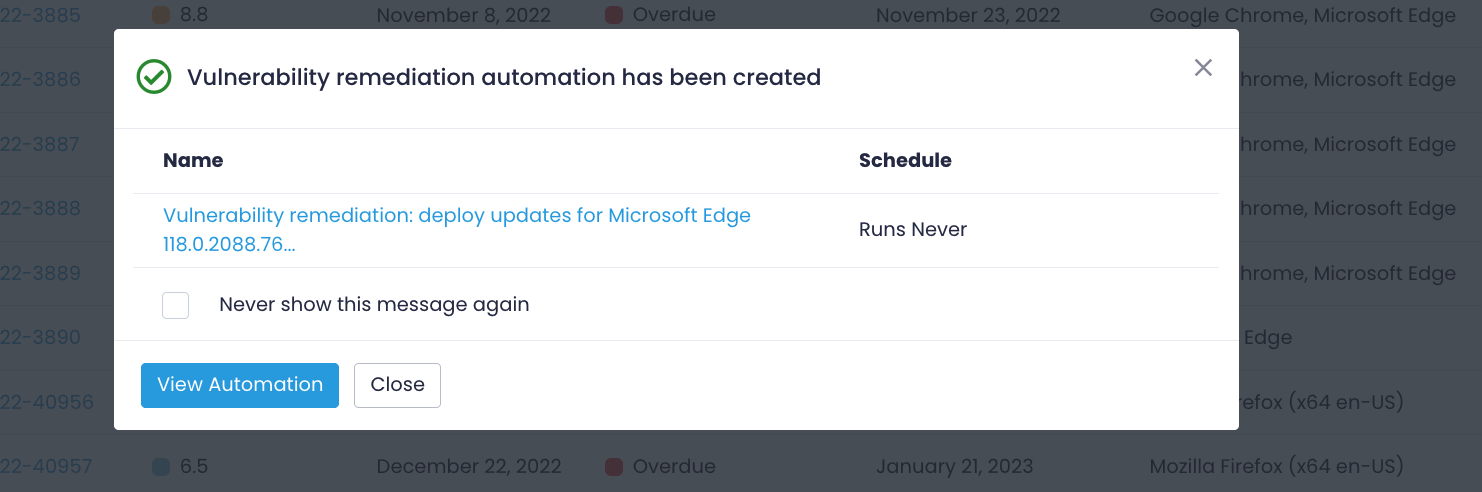
After creating a remediation policy, Action1 will automatically apply it according to the schedule. Check Automations to locate remediation actions awaiting execution. To see past vulnerability management actions, see Automation History.
Option 2: Remediation by Uninstalling a Product
Suggested option in case there is no update available or the software is out of compliance. Select Start Remediation and check selected CVEs, then choose Mark as Uninstall Product. In the next step, specify endpoints, then schedule execution. After creating a remediation policy, Action1 will automatically apply it according to the schedule. Check Automations to locate remediation actions awaiting execution. To see past vulnerability management actions, see Automation History.
Option 3: Remediation by Applying Compensating Controls
Suggested option in case there is no update available but the CVE can be handled outside Action1 by adjusting your infrastructure, network, or policies. For example, when CVE-2019-19781 was reported, Citrix ADC and Citrix Gateway didn’t have proper mitigating patches available, thus administrators were instructed to block 8080, 443, and 80 ports.
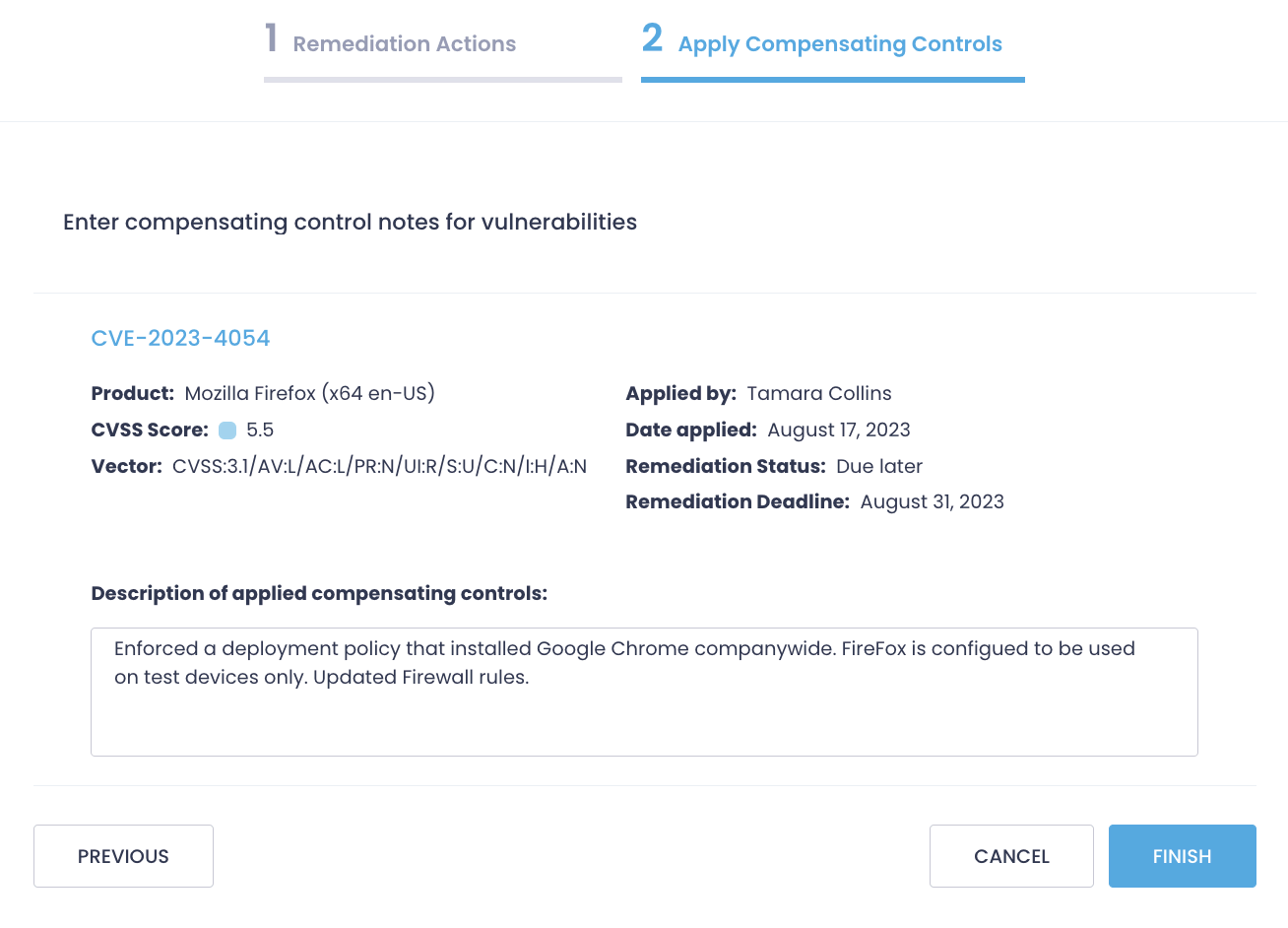
Select Start Remediation and check selected CVEs, then choose Mark as Apply Compensating Controls. In the next step, describe the steps you’ve taken. Note that you have to manually apply these controls.
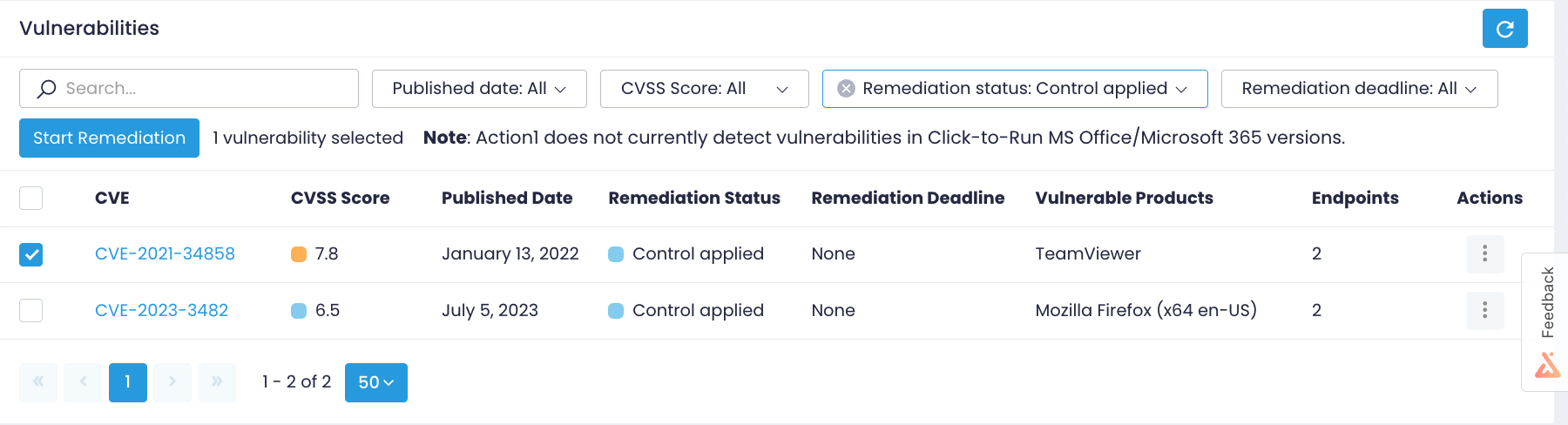
Unlike CVEs that were remediated by installing updates or uninstalling a product and turned into a policy, compensated vulnerabilities remain in the Vulnerabilities view with the Control Applied status. Filter out such CVEs by remediation status and revise them later, for example, once the update is released.