Firewall Configuration
Inbound and Outbound Connections Explained
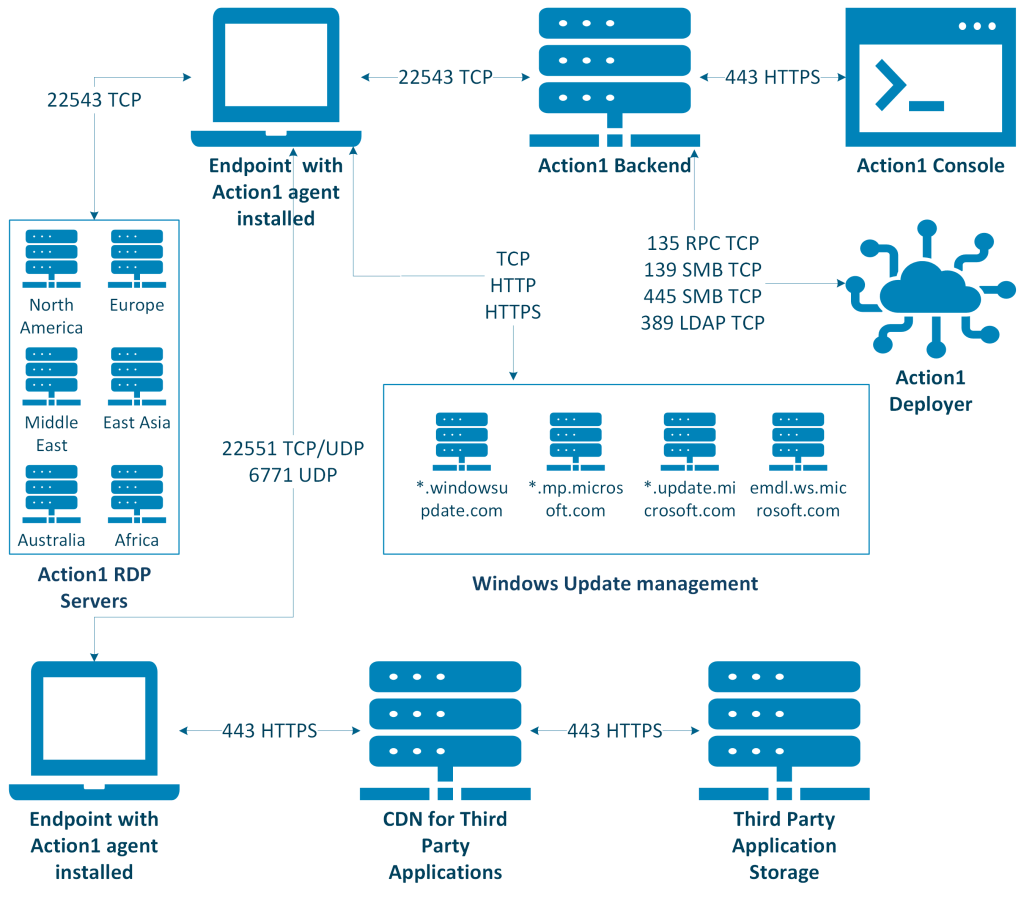
The Action1 agent always initiates outbound connections to the Action1 cloud platform. Once a connection is established, the agent maintains an open channel to receive instructions from the cloud servers, such as execution commands or data collection requests, triggered either by user actions in the Action1 Console or by scheduled tasks. For these connections, you need to configure outbound firewall rules.
An exception to the outbound-only model is peer-to-peer (P2P) software distribution: if multiple Action1 agents reside on the same local network, they can exchange software package segments directly. In such cases, agents must be capable of accepting inbound LAN connections from peers. Configuring inbound firewall rules scoped to the local network is not mandatory, but recommended to benefit from P2P functionality.
Network & Data Flow Diagram
Firewall Rule Reference
Refer to the following sections for a complete description of ports and protocols that should be configured in your system in the corresponding Action1 region: