Patch Management in Minutes with Action1
Action1 reinvents patch management with an infinitely scalable and highly secure platform configurable in 5 minutes that just works. With integrated real-time vulnerability discovery and automated remediation for both third-party software and OS, peer-to-peer patch distribution, and IT ecosystem integrations, it ensures continuous patch compliance and reduces security and ransomware risks – all while lowering costs. Action1 is certified for SOC 2/ISO 27001 and is trusted by thousands of enterprises managing millions of endpoints globally.
This quick-start guide shows how to enable patch management for third-party apps and OS in under 5 minutes.
Looking for a Quick Start Guide for macOS? Click here!
Step 1: Add Endpoints
Step 2: Manually Review and Deploy Patches
Step 3: Automate Deployment of Critical Updates
Step 4: Generate Patch Compliance Reports
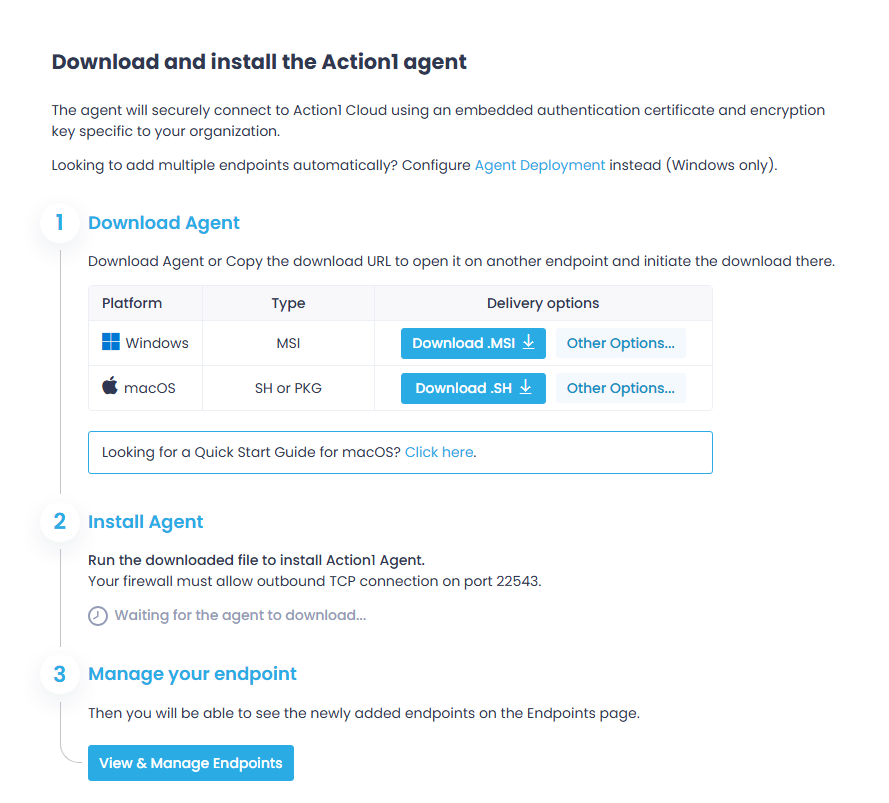
Step 1. Add Endpoints
Before you can start patching your endpoints, you need to install the Action1 Agent. It is a tiny application with a minimal system footprint, which sits idle unless an endpoint needs patching or a status refresh.
- Navigate to Endpoints and select Install Agent.
- Click Download Agent. The downloaded setup will be preconfigured with connection parameters specific to your organization.
- Install Action1 Agent.
-
- For Windows endpoint: go through the install wizard steps. In the last step, the installer will ask to elevate the privileges to install the agent. The agent is installed under the LOCAL SYSTEM account into %WinDir%\Action1 folder as a service called Action1 Agent.
- For macOS endpoint: locate the downloaded script named action1_agent_YourOrganizationName.sh and copy the script name with the extension, launch the Terminal app and run the following command, providing the script name:
bash {script_name}. This will automatically download and start the Action1 agent setup.
Go through the Agent setup wizard steps. The agent is installed under the administrative account in the /usr/local/action1 directory and operates as a daemon.
-
- Check Connection Status. Go back to Action1 Console and wait for the Action1 cloud connection check to complete.
- Go back to Endpoints page and see the newly added agent details there. It will automatically display all system information for the endpoint, such as missing updates, installed software, and hardware details.
Try later: for bulk deployment on multiple endpoints, use Microsoft Intune, Group Policy, or any of your current remote deployment tools.
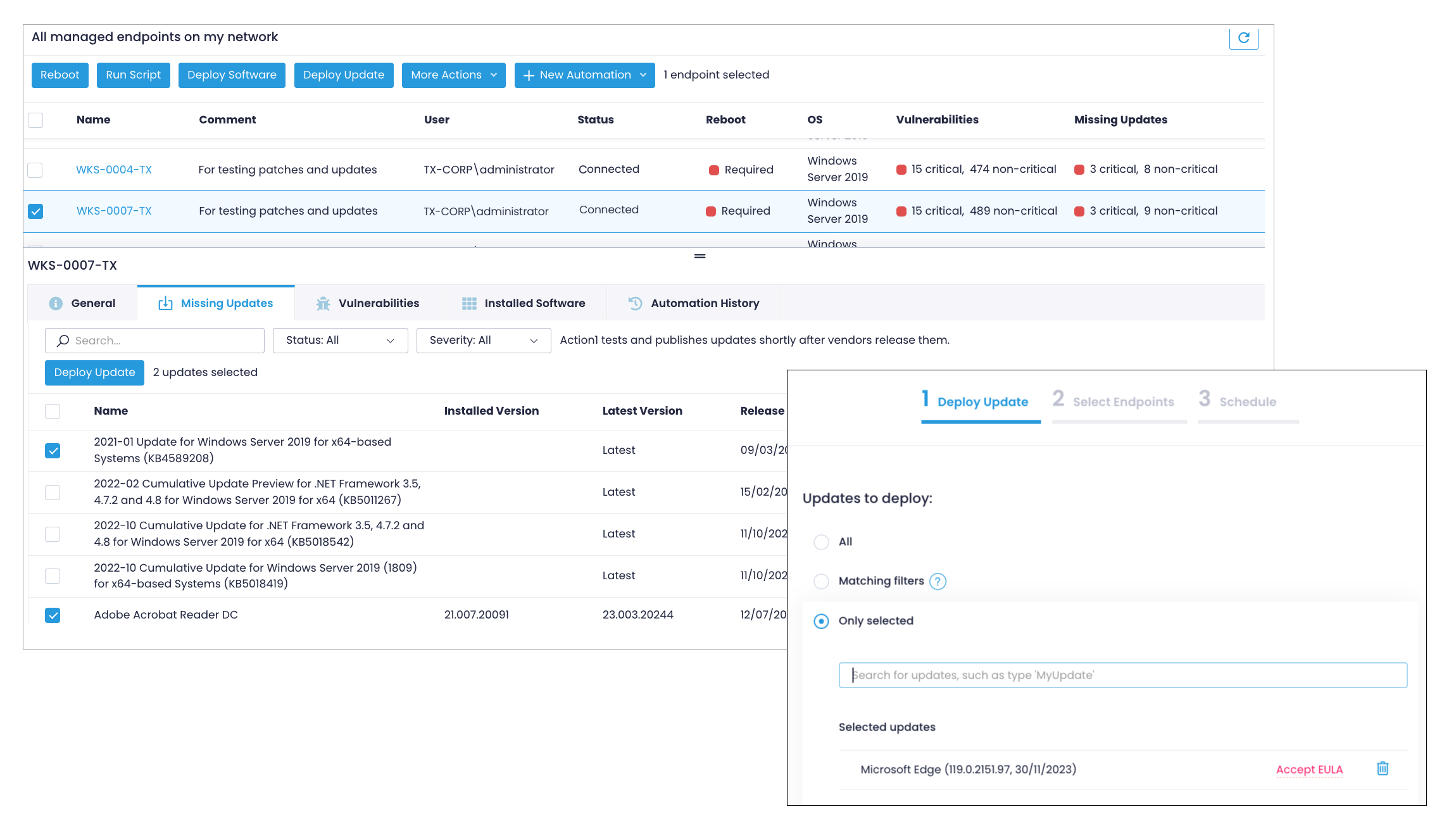
Step 2. Manually Review and Deploy Patches
All endpoint information, including missing patches, installed software, and OS details is refreshed in real time. You don’t need to schedule periodic scans to understand if any updates are missing.
- In the Endpoints section, click on the endpoint name.
- Select the Missing Updates tab and pick the updates you want to deploy. All applicable updates, both for OS and third-party apps will be shown in one view along with the update type and security severity.
- Click Deploy Update to start the update wizard. It will prepopulate the list of selected updates in Step 1.
- Adjust the Reboot Options as needed. The default is to give users up to 60 minutes to save their work if any of the updates being deployed require a reboot.
- Click Next Step twice to see the scheduling options in Step 3. Leave the default Run Now for testing purposes and click Finish.
- Action1 will begin deploying the selected updates and report status in real-time.
Try later: Check out the Vulnerabilities view to remediate vulnerabiulities.
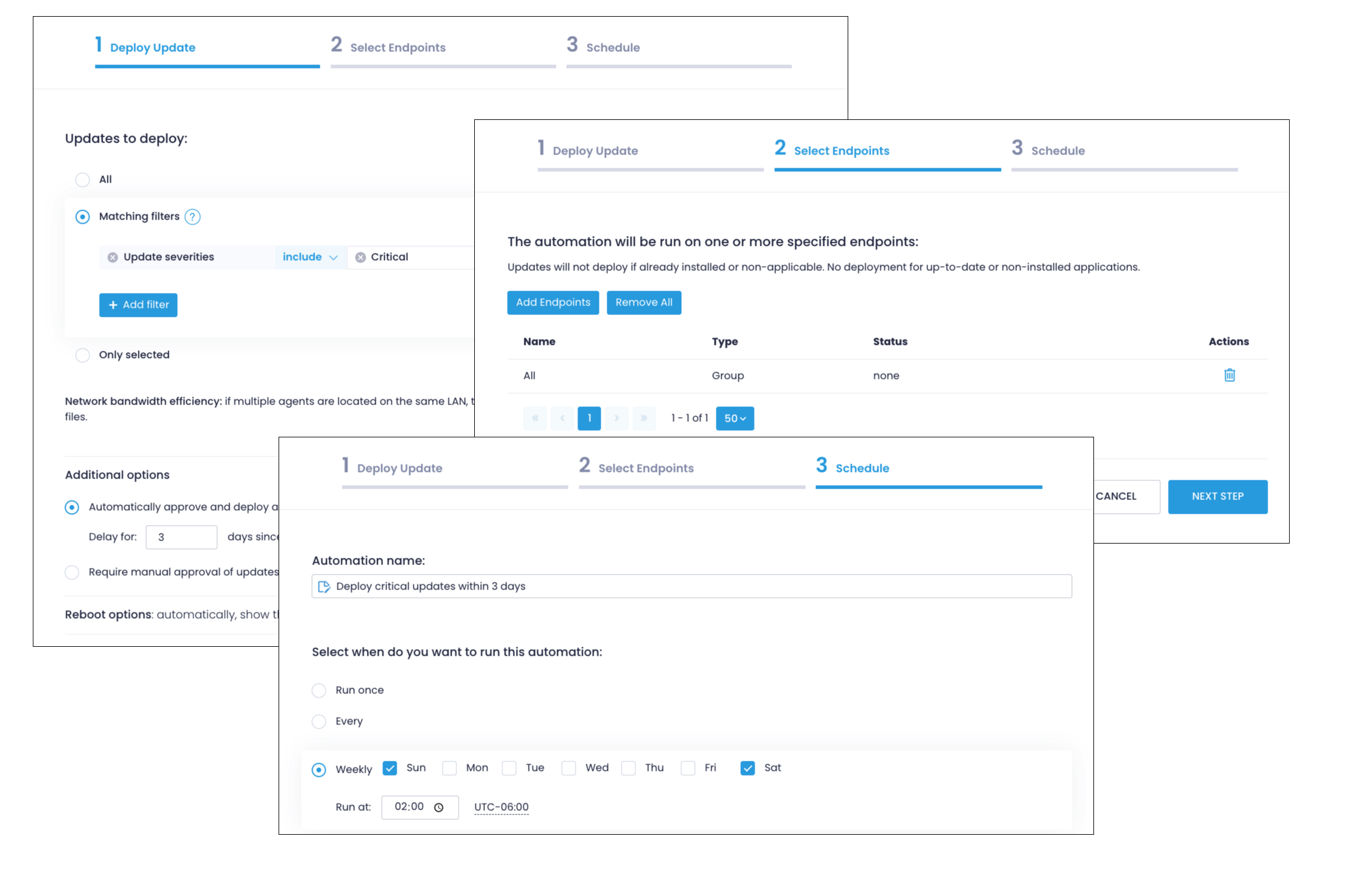
Step 3. Automate Deployment of Critical Updates
Automate patch and vulnerability management routines to ensure compliance of your endpoints, The following example configures an automation to deploy all critical security patches for OS and apps 3 days after they are released.
- Navigate Automations , select New Automation and specify Deploy Update.
- On the Deploy Update step, select Matching Filters.
- Click Add filter, select Update severities, and select Critical.
- Below the filters, click Additional options, select Automatically approve and deploy all matching updates and enter 3 days as the delay parameter.
- Adjust the Reboot Options as needed, similar to the previous step.
- Then Add Endpoints to select the endpoints or groups.
- On Schedule step, define a schedule for your automation, such as weekly, Sun&Sat at 2am.
Try later: create another automation that requires manual approval of updates and use the Update Approval section to selectively approve or decline updates. Another option is to create a broader automation to cover updates outside of critical updates.
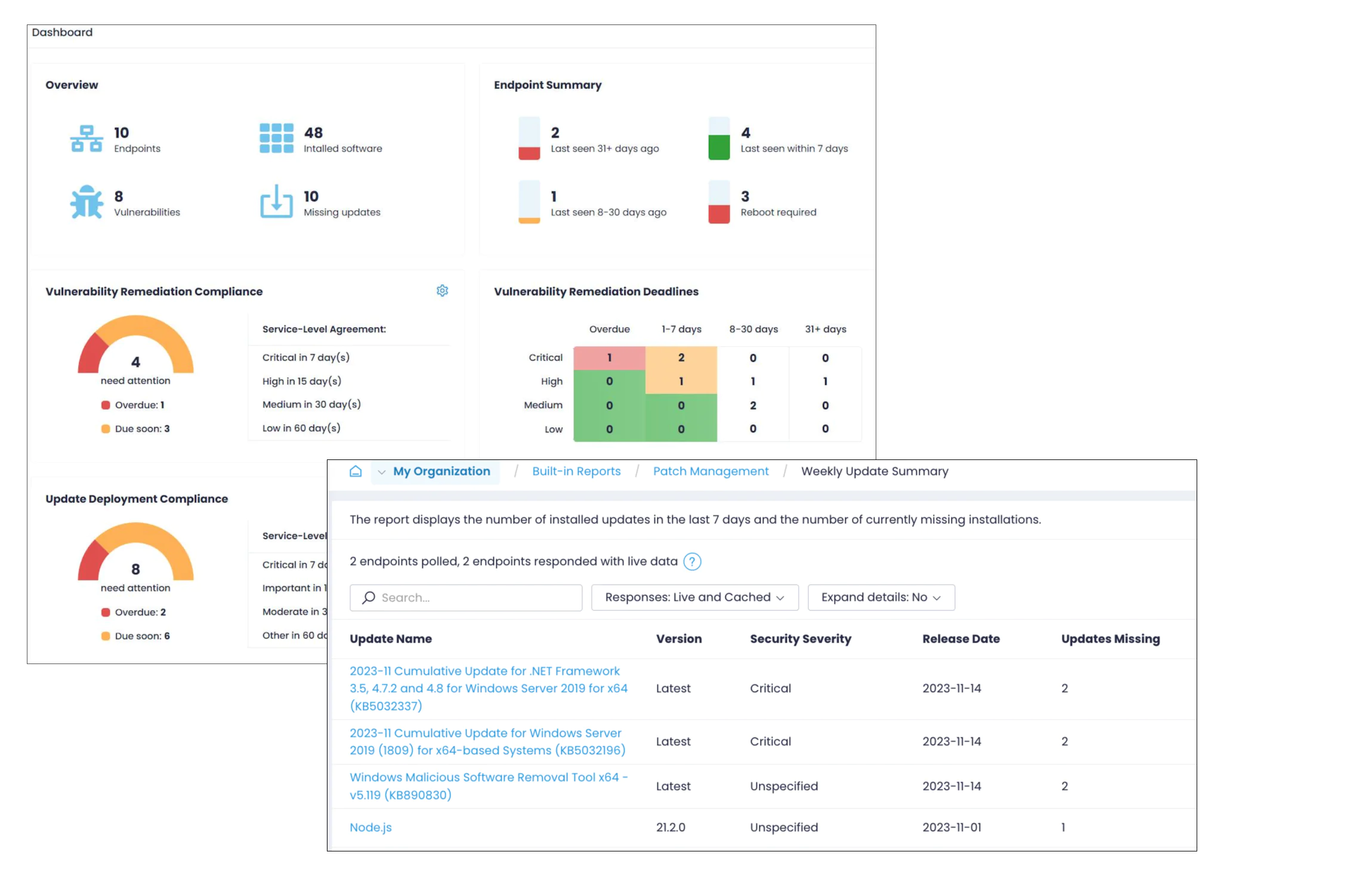
Step 4. Generate Patch Compliance Reports
Action1 comes with a real-time patch compliance dashboard and live reports to facilitate periodic reviews of your security posture and assist with compliance audits.
- Navigate to Dashboard to see a birds-eye view of your endpoints health state including vulnerability remediation compliance, pending deployments, how many endpoints need a reboot, etc.
- Go to Built-in Reports | Patch Management to generate reports on daily and weekly patch statistics, updates still missing, reboots required, and more.
- Click Tools | Subscribe within any of these reports to receive them in your email on the desired schedule (such as every Monday).
Next Steps
Action1 comes with many other capabilities to streamline your patch management. Once you are comfortable with the basics, explore the following steps:
Leverage app-based multi-factor authentication
Multi-factor authentication is an effective way to secure user accounts and access to data since it adds an extra verification step to your sign-in procedure. Email-based MFA is enabled by default; however, Action1 recommends a more secure MFA with an authentication app (such as Google Authenticator, Twilio Authy, Duo Mobile, or Microsoft Authenticator). For details, see Multi-factor Authentication.
Create endpoint groups
Segment your organization to assign different automations based on server types, department, location, OS version, and more. Navigate to Endpoints and click Create Group. For details, see Endpoint Groups
Inventory of installed software
Go to the Installed Software section to see all applications, their versions, and whether any updates are available for them. For details, see View Installed Software
Deploy applications
Remotely install and configure dozens of applications pre-configured in Software Repository. Select one or more endpoints and click Deploy to Endpoints to get started. To add a custom app, go to Software Repository and click Add to Repository to get started. For details, see Deploy Software.
Uninstall applications
Remove unneeded or legacy applications manually or automatically. Select one or more endpoints and click Uninstall Software or create an Uninstall App policy to streamline automatic uninstalls.
Run scripts
Action1 comes with Script Library to perform remote management activities, such as blocking Windows Feature Updates, deleting temp files, and more. You could also add your custom PowerShell scripts to Script Library. For details, see Script Library.