Vulnerability Management
Reports on vulnerability management help you track and remediate unresolved vulnerabilities affecting your managed endpoints. Use them to examine vulnerabilities and their attributes in detail, including severity, status, vulnerable software, and documented compensating controls.
Navigate to Real-Time Reports & Alerts / Built-in Reports / Vulnerability Management.
NOTE: This feature becomes available to Action1 users after the nearest scheduled maintenance. To discover the date for your region, navigate to Scheduled Maintenance in the Action1 Status page.
Vulnerability Summary
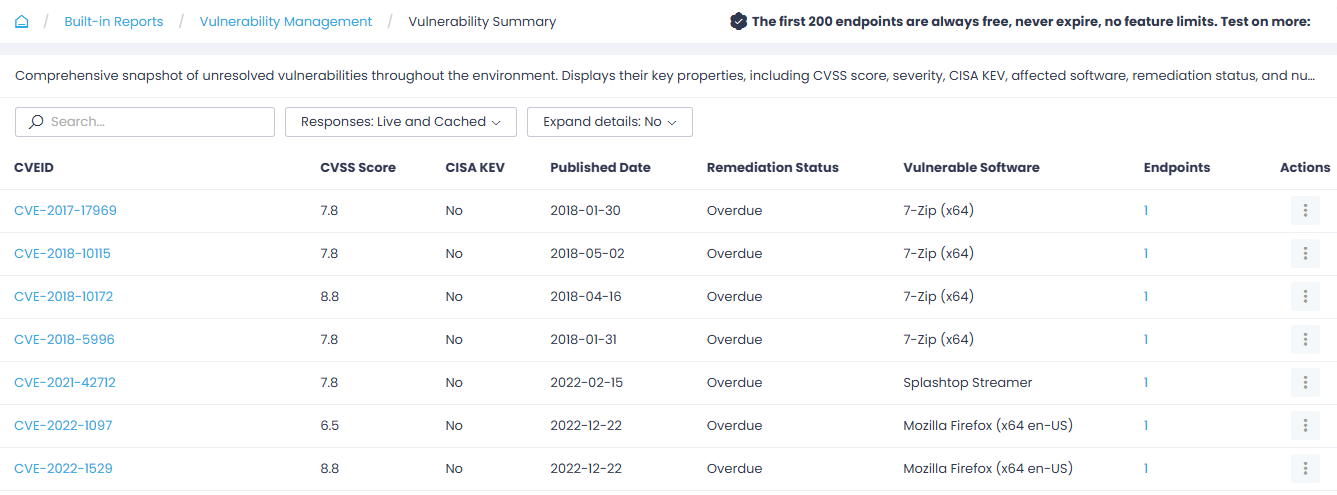
The Vulnerability Summary report provides a comprehensive snapshot of unresolved vulnerabilities throughout your Action1 organization. It displays their key properties, including CVE, CVSS score, CISA KEV, published date, vulnerable software, remediation status, and number of affected endpoints.
Click on the number in the Endpoints field to view the endpoint name and operating system for each affected endpoint, as well as vulnerable software and its version.
TIP: With Expand details set to Yes, the vulnerable software version will also be displayed.
All Critical Vulnerabilities
This report offers an up-to-date listing of critical vulnerabilities across all managed endpoints, available at a glance. Report fields are similar to those in the summary report, but only the vulnerabilities having Critical severity are included.
Known Exploited Vulnerabilities
Review the list of known exploited vulnerabilities from the CISA KEV catalog, currently affecting your endpoints. Report fields are similar to those in the summary report, but only the vulnerabilities listed in the CISA KEV catalog are included.
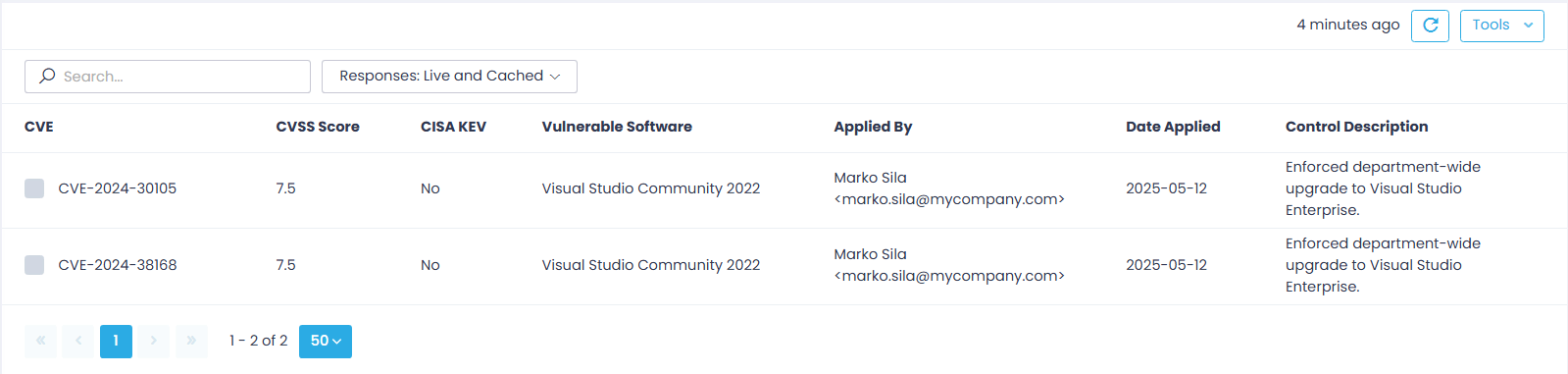
Documented Compensating Controls
This report lists compensating controls (e.g., policies or network adjustments) applied manually to mitigate vulnerabilities without software patching. You can discover who applied each control and when.
Use Tools in the top-right corner to see additional actions:
- Each report can be exported as CSV or HTML.
- To receive a report on a regular basis, select Subscribe. To learn more, see Scheduled Reports Delivery.
- Choose Create Alert to receive instant notifications on changes. To learn more, see Alerts.
- If you are interested in customizing a report, Clone it first.
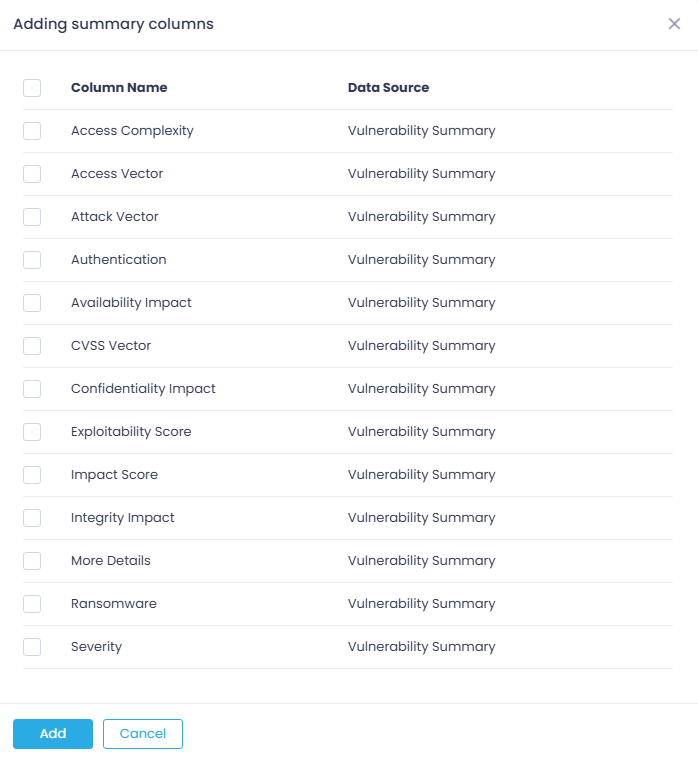
For example, if you want to enrich the report with additional data fields, Clone the report, follow the Custom Report wizard and at the Columns step add the ones you need.
Additional fields that you can use when creating custom reports on vulnerability management include:
Attack Vector, Published Date, Impact Score, Exploitability Score, Remediation Deadline, More Details (link to NVD), Access Vector, Access Complexity, Authentication, Confidentiality Impact, Integrity Impact, Availability Impact.
See also: Custom Reports