Permissions in Detail
Here is the list of available permissions you can assign to Action1 roles.
Permissions
Description
Permission scope
Implicitly included permissions*
View Automations and History,
View Updates,
View Installed Software,
View Software Repository,
View Endpoints,
Use "Deactivate Updates in Windows Settings" script
Manage Endpoint Attributes
View Data Sources
Use Scripts
View Advanced Settings for the "Identity Provider" setting from "Single sign-on" category
View Advanced Settings for the "Remote desktop" category
View Updates,
View Installed Software,
View Software Repository,
View Endpoints,
Use "Deactivate Updates in Windows Settings" script
View Installed Software,
View Updates,
View Endpoints,
View Vulnerabilities,
View Advanced Settings for the "SLA" category
View Installed Software,
View Vulnerabilities,
View Reports (on system updates)
Notes
- within Enterprise scope, you can assign any user any role
- within Organization scope, you can assign any user to organization-specific roles only
- with Login Email Wildcard scope, you can select certain organization and then assign organization-specific roles to the users with the specified emails - or select All Organizations and then assign any role to these users.
- If Organization was chosen as permission scope, then creation, cloning, modification, and deletion will be allowed if the advanced setting's own scope contains only the scopes related to the selected organization.
- Creating an automation for a group of endpoints is only allowed if all endpoints in the group are visible. Visibility may be limited if the group contains endpoints that belong to another group excluded by the View Endpoints permission. Similarly, specifying individual endpoints by ID is restricted if those endpoints are part of a group that has been excluded through the View Endpoints permission.
Deploy Updates automation:
- To disable automatic Windows updates during the automation execution, the "Deactivate Updates in Windows Settings" script is used. So, the underlying Use Scripts permission will be granted automatically, with the Script permission scope and 'Include scope' set to that script only.
- To use the 'Auto-approve updates' option, the Approve Updates permission will be required.
Run Script automation:
- To use the ad-hoc scripts or scripts from the Script Library, the Use Scripts permission will be required:
- Using scripts from the Script Library will require the Script scope.
- Using ad-hoc scripts will require the Ad-Hoc Script scope.
The only exception is the Use Script permission, which may have Enterprise scope.
The list of displayed roles will be filtered to exclude those that are not accessible.
To assign/unassign a role to/from user, the Assign Roles permission is required (see its description above).
- Using scripts from the Script Library will require the Script scope.
- Using ad-hoc scripts will require the Ad-Hoc Script scope.
-If 'Exclude' scope was configured for a Script permission scope, the excluded scripts will be filtered out from the list.
-If 'Include' scope was configured for a Script (but not for Enterprise) permission scope, only the scripts with 'Include' scope will be displayed in the list.
- if the included Organization is absent, all endpoints from the included Groups will be displayed.
- if the excluded Groups are present, all endpoints belonging to them will be filtered out.
For viewing endpoints from a certain group: if an excluded Group is present, all endpoints belonging to it will be filtered out.
Reports and a list of installed software will display data for a certain endpoint(s).
- If selected, this will allow or restrict access to a specific report within a specific organization.
- If omitted, access will be granted to the specific report across all organizations.
Important! With the latest version of the Action1 solution, the Manage Roles permission no longer provides the ability to assign roles. Instead, you should use the Assign Roles permission (note that it is not implicitly included in the latest version of Manage Roles). If you rely on the Manage Roles permission, you must explicitly grant the new Assign Roles permission.
Example
You want to allow the helpdesk team to view all built-in reports except for “Group Membership” and “Logon Statistics” reports for the target organization “My Organization”. For that, you can take these steps:
- Create a role named Helpdesk.
- When setting up its permissions, select View Reports permission.
- Next, when configuring the scopes, click Exclude scope and select Report.
- From the list of organizations, select My Organization, and from the list of reports, select “Group Membership”.
- Click Add, then repeat steps 3 and 4 for the “Logon Statistics” report.
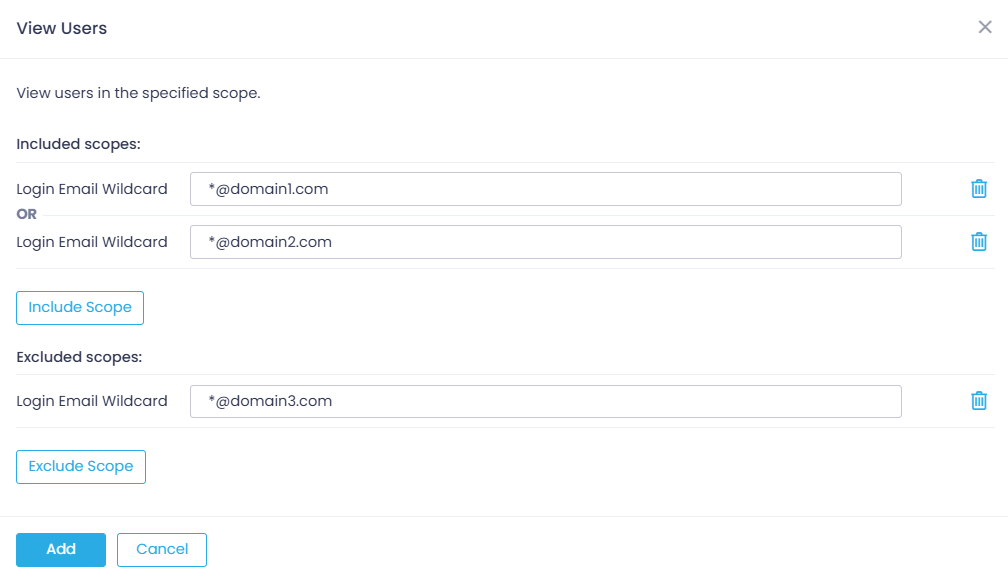
**) – Login Email Wildcard scope enables isolation of user visibility by domain, which is specified using a wildcard: *@mydomain.com
You can use this scope, for example, with:
- Manage Users – to allow inviting only users from the specified domain to Action1.
- View Users – to prevent users in one organization from seeing the users in other organizations or domains within the same Action1 account.
Example
To include or exclude a user:
- For a single user, enter the email as usual, i.e.,
[email protected] - You can use a mask like
[email protected](here ? means any single character) or a mask likenam*@domain.com(here * means any number of characters)
To include or exclude several domains or users:
Use Include Scope or Exclude Scope for each email.
How are multiple permissions combined?
Permissions do not override each other, but combine with each other. However, consider that the Exclude scope always takes priority over Include, and you can use it to explicitly deny what the implicit permission grants.
Example
The Manage Endpoints permission implicitly grants access to view endpoints within the specified scope. Thus, if a user was assigned the Manage endpoints permission for Org1, this user will be implicitly allowed to View endpoints in Org1.
- If this user is also explicitly assigned View Endpoints permission for Org2, the resulting permission for this user will allow to View Endpoints for both Org1 and Org2.
However, since Exclude always takes priority over Include, you can explicitly deny what the implicit permission grants. In this example, you can exclude View Endpoints permission for the target user, e.g., on a group in Org1 named “Sensitive Group”.
- The resulting View Endpoints permission will allow viewing only the endpoints in Org1, and only those that are not members of “Sensitive Group”.