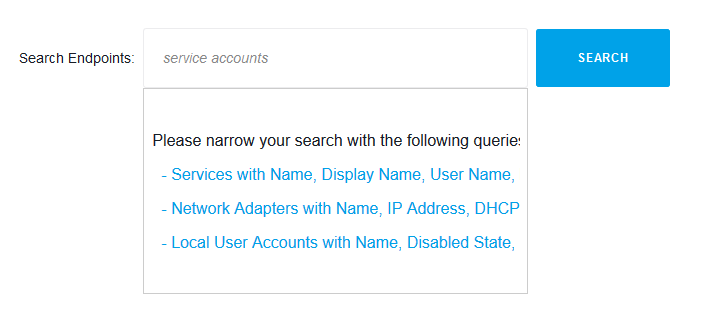
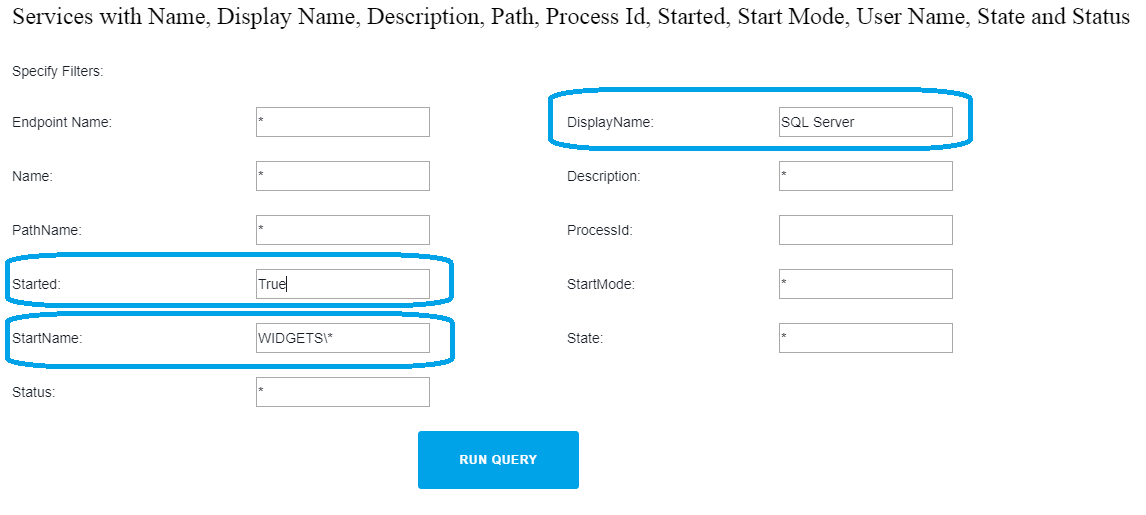
Action1 is a free cloud-based patch management solution. Among hundreds of other built-in features such as remote patch deployment, remote access, it allows running reports to find all SQL Server service accounts used on endpoints. After the discovery is done, you can manage service account passwords and perform other maintenance operations. This article explains how to list Exchange service accounts using Action1 to find service accounts in domain Windows server 2008 r2 or other operating systems and also shows how to list service accounts from the command line for organizations that are not able to utilize Action1 in their environments.
Manually:
1. Execute WMI Query in ROOT\CIMV2 Namespace:
- Launch WMI Explorer or any other tool which can run WMI queries.
- Run WMI query: SELECT * FROM Win32_Service
2. Open WMIC Command-line Interface:
- Press WIN+R
- Type “wmic”, press Enter
- In wmic command line tool type: /node:RemoteComputerName service
3. Run This Simple Windows Powershell Script:
Thru WMI object: Get-WmiObject -Namespace ROOT\CIMV2 -Class Win32_Service -Computer RemoteComputerName
4. Use Following Code to Select Specific Columns:
Execute: Get-WmiObject -Namespace ROOT\CIMV2 -Class Win32_Service -Computer RemoteComputerName | Select-Object DisplayName, Started, StartMode, StartName, PSComputerName
5. Sort the Results Using the Line Below:
Invoke command: Get-WmiObject -Namespace ROOT\CIMV2 -Class Win32_Service -Computer RemoteComputerName | Select-Object DisplayName, Started, StartMode, StartName, PSComputerName | Sort-Object DisplayName
6. The Next Code Helps to Filter Results:
Use it: Get-WmiObject -Namespace ROOT\CIMV2 -Class Win32_Service -Computer RemoteComputerName | Select-Object DisplayName, Started, StartMode, StartName, PSComputerName | Where-Object -FilterScript {$_.DisplayName -like “*SQL Server*”}
7. Save Results to CSV File:
Run: Get-WmiObject -Namespace ROOT\CIMV2 -Class Win32_Service -Computer RemoteComputerName | Select-Object DisplayName, Started, StartMode, StartName, PSComputerName | Export-CSV “c:\file.csv” -Append -NoTypeInformation
8. The Next Step Is to Query Multiple Computers:
Computers from a text file: Get-Content -Path c:\computers.txt | ForEach-Object {Get-WmiObject -Namespace ROOT\CIMV2 -Class Win32_Service -Computer $_}
– computers from AD domain: Get-ADComputer -Filter {OperatingSystem -Like ‘Windows 10*’} | ForEach-Object {Get-WmiObject -Namespace ROOT\CIMV2 -Class Win32_Service -Computer $_.Name}