Update Management Software
Action1 keeps your on-premises and remote endpoints secure and up to date by automating deployments of OS and third-party patches. The platform addresses vulnerabilities, fixes bugs, adds new features, and improves endpoint performance to boost security, reduce the attack surface, and prevent unexpected downtime.
Trusted by many Fortune 500 companies


Update Management Software Benefits
Automated Update Management
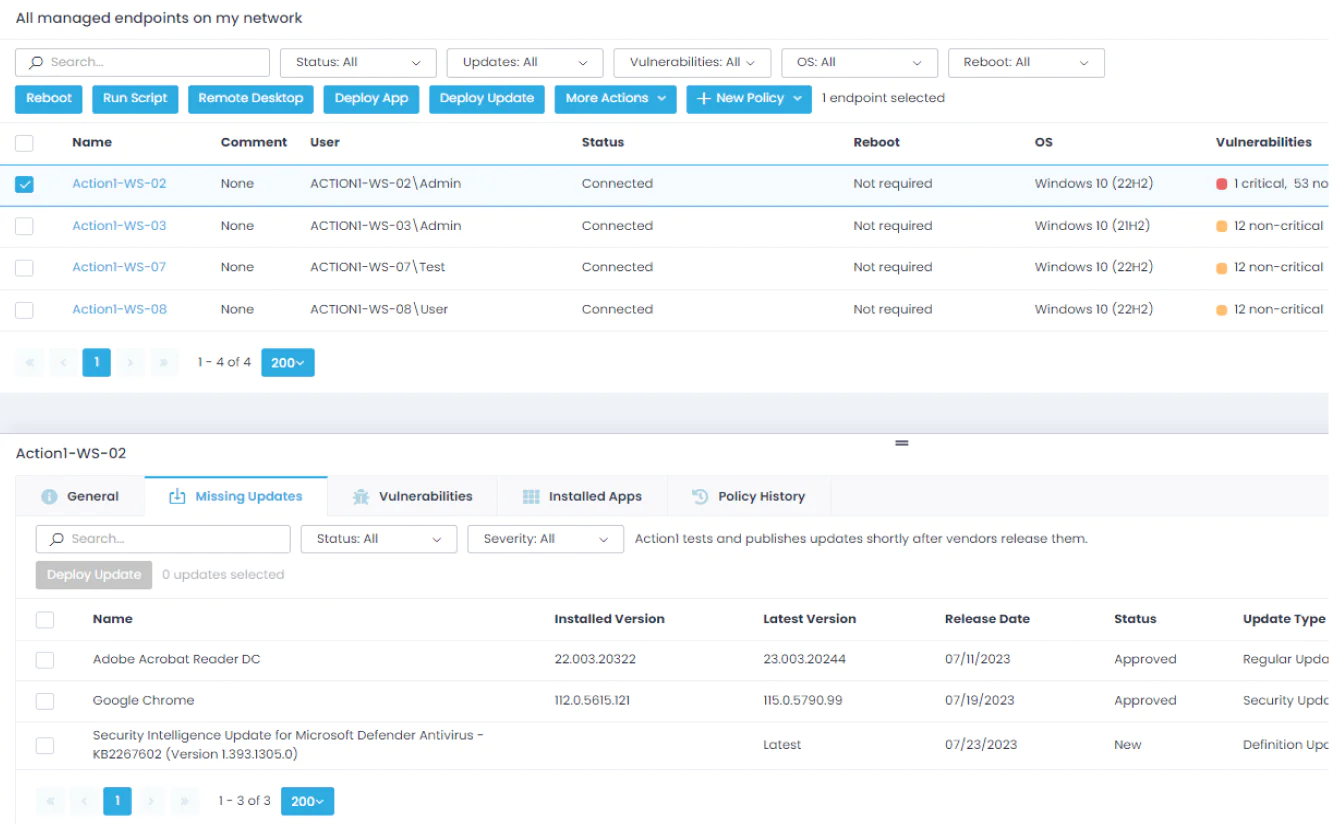
Automate each step of the update process. Once installed, Action1 detects vulnerabilities, lists missing updates, offers test features, deploys updates immediately or on schedule, and generates reports with a few clicks.
Rapid Vulnerability Remediation
Stop software vulnerabilities before they become real threats. Action1 identifies the highest-risk flaws and automatically deploys critical updates faster than cybercriminals can exploit them. This intelligent approach maximizes your endpoint security while requiring minimal effort from your team.
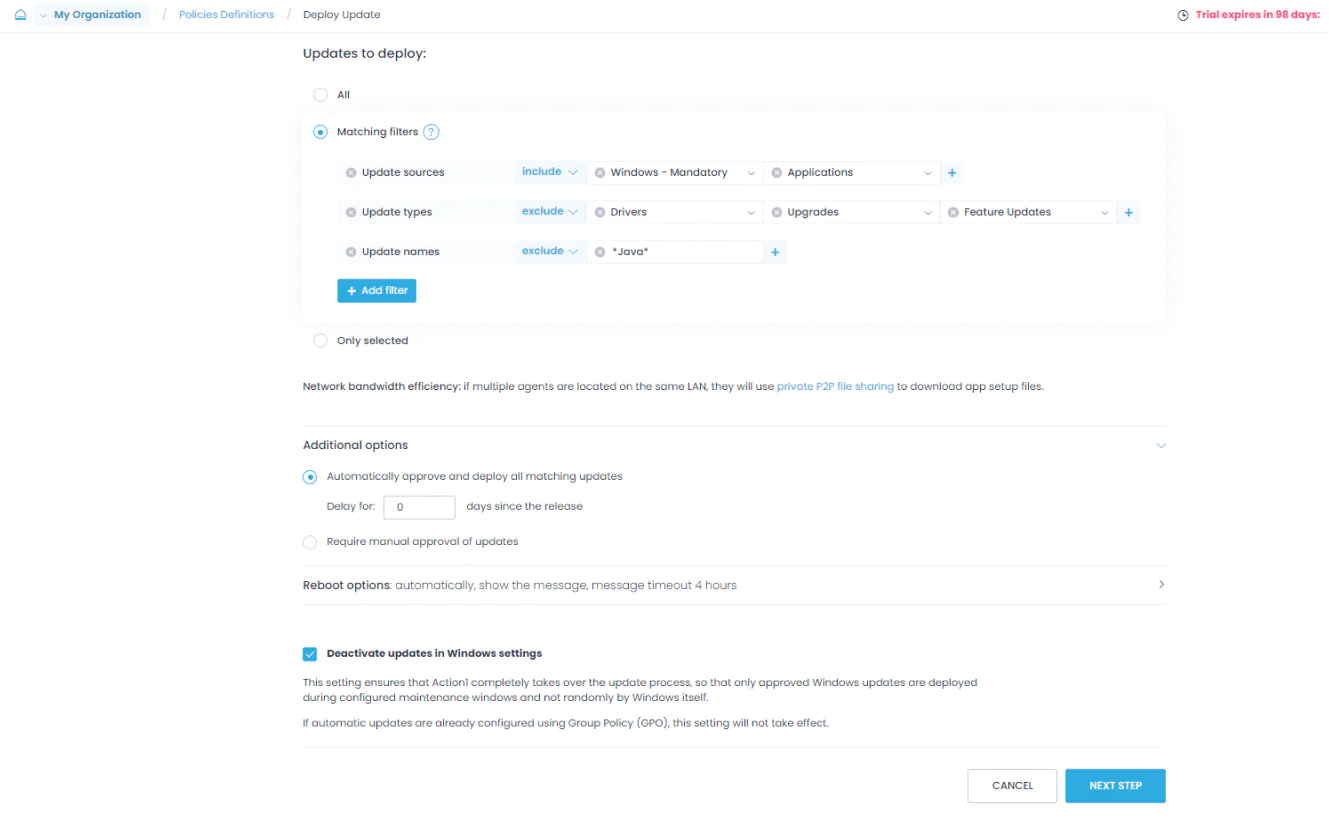
OS and Third-Party Patching
Identify missing OS and third-party updates across all of your on-premises and remote endpoints. Schedule deployments and test them via customizable update rings before reaching your production environment.
Boosted Productivity
Schedule, test, and deploy updates outside business hours to prevent operational disruptions that decrease productivity. These updates fix software bugs, introduce new features, and keep your systems secure and optimized.
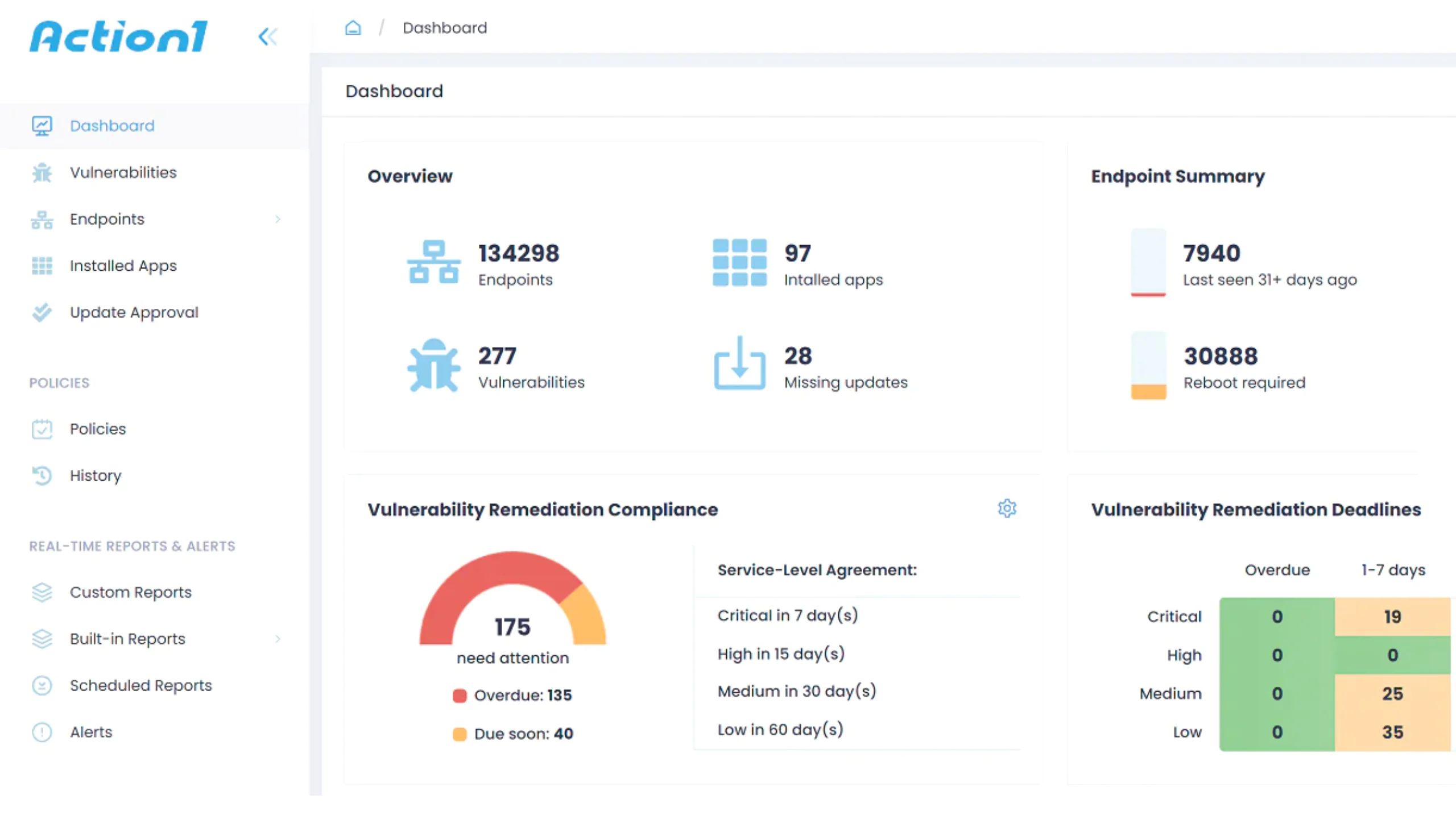
Real-time Reporting
Monitor every endpoint’s update status across your network in real time, regardless of location. Create detailed reports and receive them via email or export them to CVS format.
Minimized Business Disruption
Schedule patching outside peak hours or use staged deployment to avoid impacting productivity. Keep systems updated without interrupting users or critical operations.
The Need for Update Management Software
Lightning-fast Deployments
Update your on-premises and remote endpoints with ease, speed, and accuracy throughout automated deployments. Action1’s privately maintained secure software repository ensures only tested OS and third-party updates reach your systems, while the P2P update distribution minimizes external bandwidth usage and ensures rapid deployment of large updates without any on-prem cache servers.
Minimize Downtime Risks
Forget about unexpected downtime since you can schedule, test, and deploy updates outside business hours using end-to-end automation. The update rings feature allows only reliable updates to be deployed across your endpoints while stopping those that don’t meet success rates and deployment counts. With Action1, you strengthen the security posture across your network without sacrificing business continuity.
Maintain Software Compliance
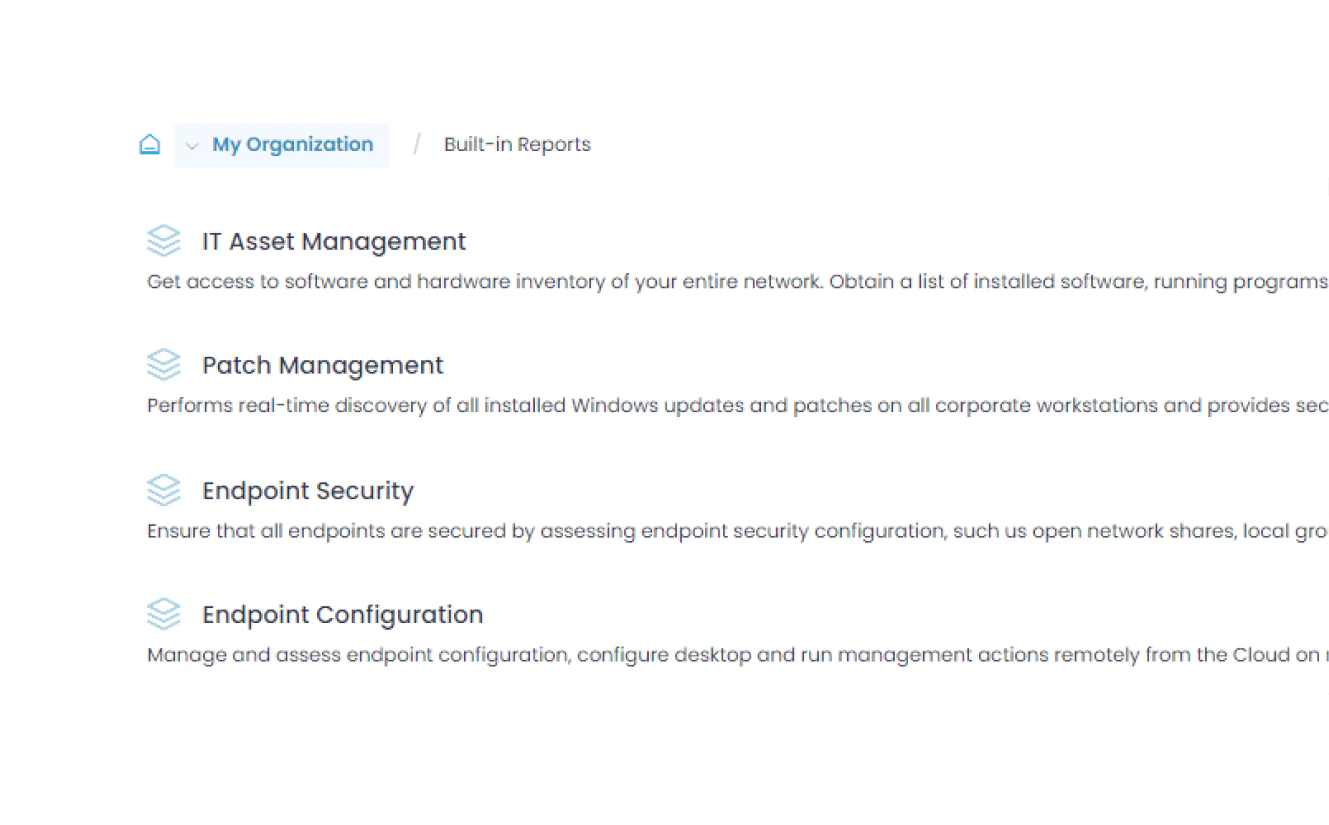
Generate detailed compliance reports to stay audit-ready with just a few clicks. Action1’s 100+ built-in templates cover update management, software and hardware inventory, and security configurations. Whenever needed, you can customize existing reports by adding or removing columns, adjusting filters, and modifying grouping criteria to achieve regulatory compliance.
Strengthen Security Posture
Unpatched systems are prime targets for cyberattacks and ransomware. Regular update management ensures that security vulnerabilities are addressed promptly, minimizing exposure windows and protecting critical business data from exploitation.
Simplify IT Operations
Without centralized update management, IT teams spend countless hours manually identifying, testing, and deploying patches. A unified solution streamlines these tasks, reducing complexity while maintaining consistency across all managed devices and environments.
Simplify Regulatory Compliance
Staying compliant with standards like NIST, CIS, and ISO requires documented patching practices. Update management software automates reporting and provides clear audit trails, simplifying evidence collection for compliance checks.
Action1 Software Update Management
Keeping your endpoints secure, updated, compliant with regulatory standards, and running smoothly has never been easier. Start remediating software vulnerabilities with confidence and precision, without disrupting your daily operations.
Central Dashboard
Available from your web browser, Action1 keeps all of your managed endpoints accessible at your fingertips virtually from anywhere in the world.
Robust and flexible automation
Automate patching across your servers and apps with just a few clicks. Schedule update deployments at a convenient time or during off-peak hours to avoid any operational disruptions.
Visibility with Reports and Alerts
Get real-time insight into your network’s current patch status with customizable reports and alerts—so you always know what’s updated, what’s vulnerable, and what needs attention.
Cloud Patch Management
Manage and patch your Windows servers from anywhere. No VPNs, no complex setup, no bandwidth issues—just fast, secure, cloud-native control over all your endpoints.
Certifications and Compliance
Action1 adheres to globally recognized standards and regulations, underscoring our commitment to security:

SOC 2 Type II

ISO 27001

TX-RAMP

CSA
CISA Secure by Design

CAIQ

GDPR
What Our Customers Say
A lot of value from Action1 comes from the peace of mind, knowing that your patches are installed, that you are protected from known vulnerabilities which attackers are likely to target with ransomware and other malware.
Action1 saves me 10–15 minutes per machine on software deployment. I can access every device remotely, so I don’t have to literally travel to every location and touch every machine.
Action1 helped us save about 125 hours per month by automating patch management. That’s a huge enabler to our business; as an MSP, the more you automate, the more money you save, and the more savings you can pass on to your customers.
Frequently asked questions
What are the key features to look for in update management software?
The key features to look for are automated update deployments across Windows, macOS, Linux, and third-party applications. The tool must be able to automate each step of the update process: endpoint discovery, vulnerability identification, risk-based prioritization, testing, scheduled deployments, and detailed reporting for compliance audits.
Through completely automating the update management process, you can keep on-premises and remote endpoints up-to-date with the latest security and feature updates, thus addressing vulnerabilities in a timely manner and ensuring smooth device performance.
For seamless business scaling, choose cloud-native update management tools that don’t require hardware infrastructure investments and can efficiently scale from hundreds to thousands of endpoints—essential for your company’s long-term success. Last, but not least, look for solutions that integrate seamlessly with your existing IT infrastructure to maximize operational efficiency.
How does update management software improve IT security and compliance?
Update management software hardens your security posture by keeping every single endpoint in your organization running with the latest security updates. With such a tool, your IT team can remediate critical software vulnerabilities as quickly as possible before cybercriminals can exploit them by deploying updates once they are released by the OS and third-party application vendors.
Through automating update deployments, the attack surface across your endpoints is significantly reduced. These solutions equip your company with the ability to generate detailed audit trails after each update deployment, which are required for compliance frameworks like PCI DSS, HIPAA, GDPR, and SOX.
This process not only keeps your systems compliant with these regulatory standards but also eliminates manual documentation efforts, taking the pressure off your IT team’s shoulders.
How do update management tools handle version control and rollback options?
Version control in update management tools involves tracking and documenting every software change made across your endpoints. This approach maintains a detailed chronological history of which applications or updates were installed, when they were deployed, and on which specific endpoints.
For rollback options, the best update management tools provide a built-in feature that creates application backups, or restore points, before deploying updates. This gives you a “plan B” and the ability to roll back problematic updates that could cause downtime or compatibility issues.
Furthermore, tools like Action1 also equip you with deployment rings, also known as “update rings,” which enable staged rollouts. These allow you to thoroughly test updates on non-critical systems or test groups of endpoints first before reaching every endpoint across your network.
This means that if an update fails and doesn’t meet your established success rates and deployment counts, it won’t advance to the outer rings, effectively preventing unexpected downtime.
What types of devices and operating systems are supported by most update management solutions?
Update management solutions support Windows, macOS, and Linux-based endpoints and servers. Keep in mind that these tools can also support mobile devices (iOS and Android), IoT endpoints, and network infrastructure components. Additionally, with these systems, you can update third-party applications across your network. However, not all of them offer this cross-platform support, which is why choosing the right tool is crucial. Cloud-based update management solutions are preferred since they can successfully manage both on-premises and remote devices from a single console directly from your browser.
How does automated update deployment reduce downtime and improve system reliability?
Automated update deployment helps your organization avoid unexpected downtime by scheduling updates during off-business hours or predetermined maintenance windows. This way your employees can finish their workday without being interrupted by update deployments. Furthermore, through automating each step of the update process, such as vulnerability identification, testing, deployment, and reporting, the time needed to secure your systems is reduced to minutes instead of days when done manually. This approach helps you to address vulnerabilities before they’re exploited, preventing costly security incidents.
