Table of Contents:
What version of Windows server do you need to use 100 new commands
Familiarity with PowerShell command blocks: Get and Add
Simple script to set the DNS server IP addresses on a network card based on its name
Change DNS Address Remotely with Action1
Betweentimes you need to update multiple computers with DNS settings. Instead of doing this one by one manually you can automate it so it can be done in one go, from a plain PowerShell script. It’s simple but very effective. This article shows how to remotely change DNS settings.
If you are administering DNS on Windows Server systems, you may have heard about Dnscmd, a powerful command-line tool that allows you to perform almost any DNS management task. Without detracting from the merits of Dnscmd, I am pleased to announce that now DNS administrators have gained a new support group in the face of 100 PowerShell teams. In this article I will talk about three of them, and also give an example of how one simple powerful tool of PowerShell can be made even more powerful.
1. What Version of Windows Server Do You Need to Use 100 New Commands
I have not had time to try out the entire hundred, but, as far as I can tell, to use them with respect to Windows Server 2008 R2, it is enough to have a Windows 8 workstation that is joined to the domain and on which the remote server administration tools (RSAT) for Windows 8. To display a list of 100 DNS commands, use the following command:
get-command *-dnsserver*
If you are running Windows Server 2012, then simply install the built-in DNS management tools, and the DNS commands will be at your disposal.
2. Familiarity with PowerShell Command Blocks: Get and Add
As you probably already understood, familiarity with the blocks of PowerShell commands should begin with testing the Get- commands. Get-dnsserveredns gives information about whether the DNS server has DNS extensions enabled (I have enabled). Get-dnsserverrecursion lets you know if a server is accepting DNS requests for zones that do not exist on this server. Suppose I request from a local DNS server serving AD, the resource www.microsoft.com. The local DNS server does not work with the public Microsoft zone, and it will perform requests to Internet resources only after recursion is enabled.
Why is this feature useful? Unfortunately, in recent years, the number of attempts to use DNS servers to organize malicious distributed denial of service (DoS) attacks has greatly increased, forcing administrators to disable recursion on DNS servers (it is enabled by default). In such cases, it is useful to be able to verify this DNS server or use the excellent means of remoting PowerShell. For example, if there are five DNS servers D1, D2, D3, D4 and D5, then a simple report on their recursion status can be displayed using the command:
invoke-command -computername d1,d2,d3,d4,d5 -scriptblock {get-dnsserverrecursion|select pscomputername,enable}
We know that the –scriptblock parameter allows braces to give remote computers a command that should be executed. In this case, there is a DNS command in curly braces, followed by a Select statement with the name of the computer on which to run this command, as well as the result.
In Server 2012, one of the time-saving DNS commands is add-dnssecondaryzone. I discovered it by setting up a new DNS server as a secondary server for a specific group of DNS zones. Setting up a secondary DNS server for an existing domain using a graphical interface or Dnscmd is a trivial task. As it turned out, you can configure the secondary DNS server for the bigfirm.com domain with the main IP address 71.23.1.5 and save the zone data to a text file bigfirm.com.dns using the following command:
add-dnssecondaryzone bigfirm.com “bigfirm.com.dns” 71.23.1.5
I assumed that this could be done immediately with seven domains, for which it would be enough just to change the name of the zone in two places. First, I saved the domain names into an array, which is a comma-separated list of names in quotes:
$zones=“bigfirm.com”,“minasi.com”,“mmco.com”,“pungogrill.com”,“thesoftwareconspiracy.com”,“softwareconspiracy.com”,“steadierstate.com”
Then, using the pipeline and the foreach-object command, I organized the transfer of the name of each zone to the add-dnssecondaryzone command using the built-in variable $ _, the contents of which is what is currently in the pipeline:
$zones | foreach-object {Add-DnsServerSecondaryZone $_ $_+“.dns” “71.23.1.5”}
It worked right away.
3. Example of Simple Script to Set the DNS Server IP Addresses on a Network Card Based on Its Name
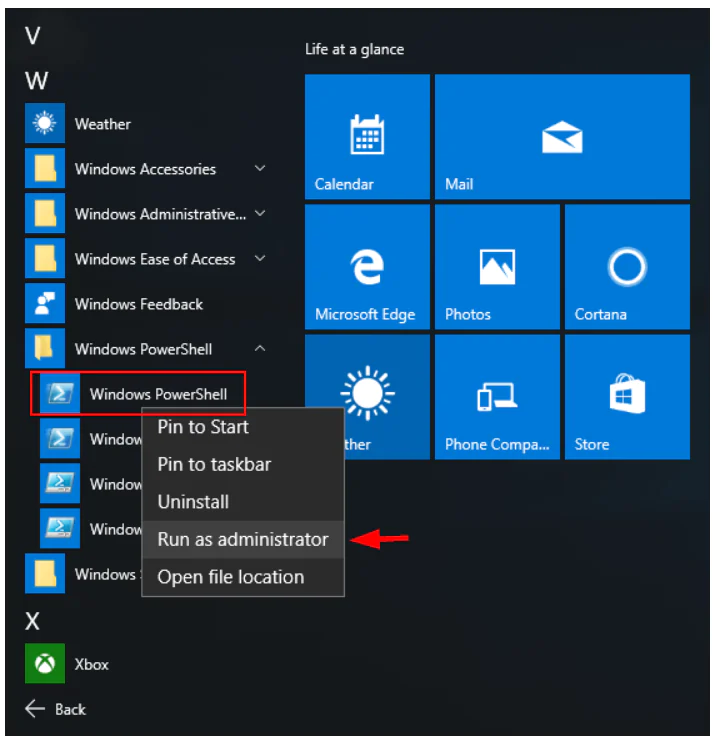
Click Start, type PowerShell, and then click Windows PowerShell.
4. Change DNS Address Remotely with Action1
Action1’s intuitive dashboard helps optimize routine tasks, significantly scaling up IT productivity.
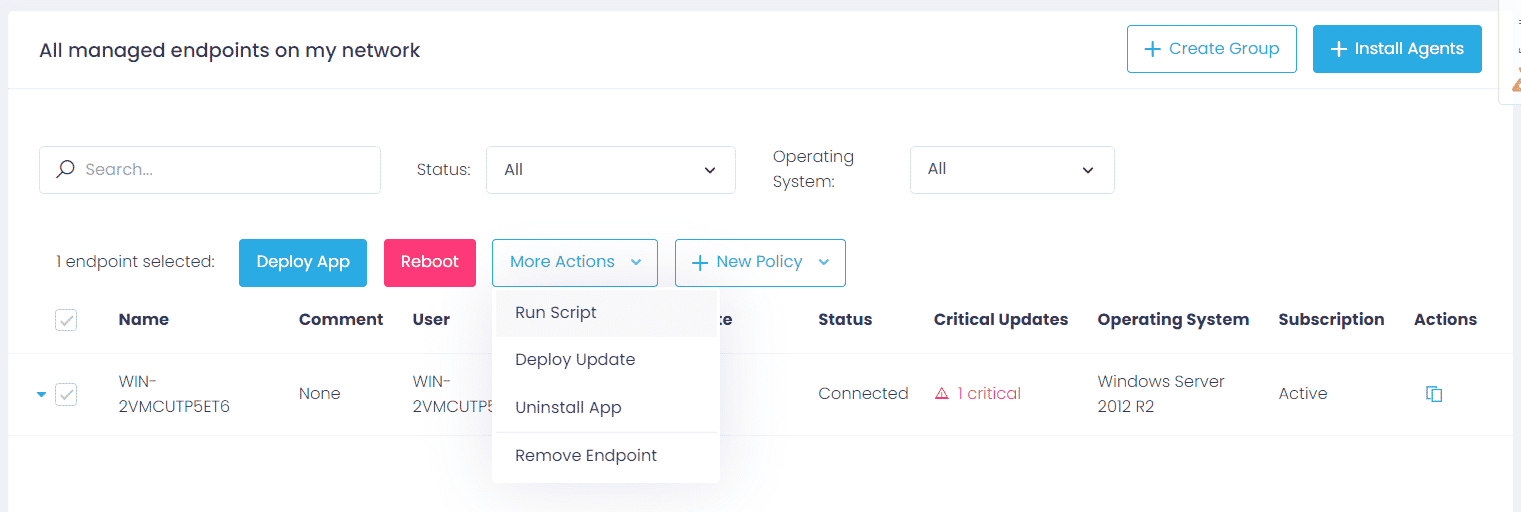
Step 1: After logging into the Action1 dashboard, in the Navigation pane (the left column), select Managed Endpoints and mark the endpoint to change DNS remotely.
Step 2: Then click on the More Actions menu and select Run Script.
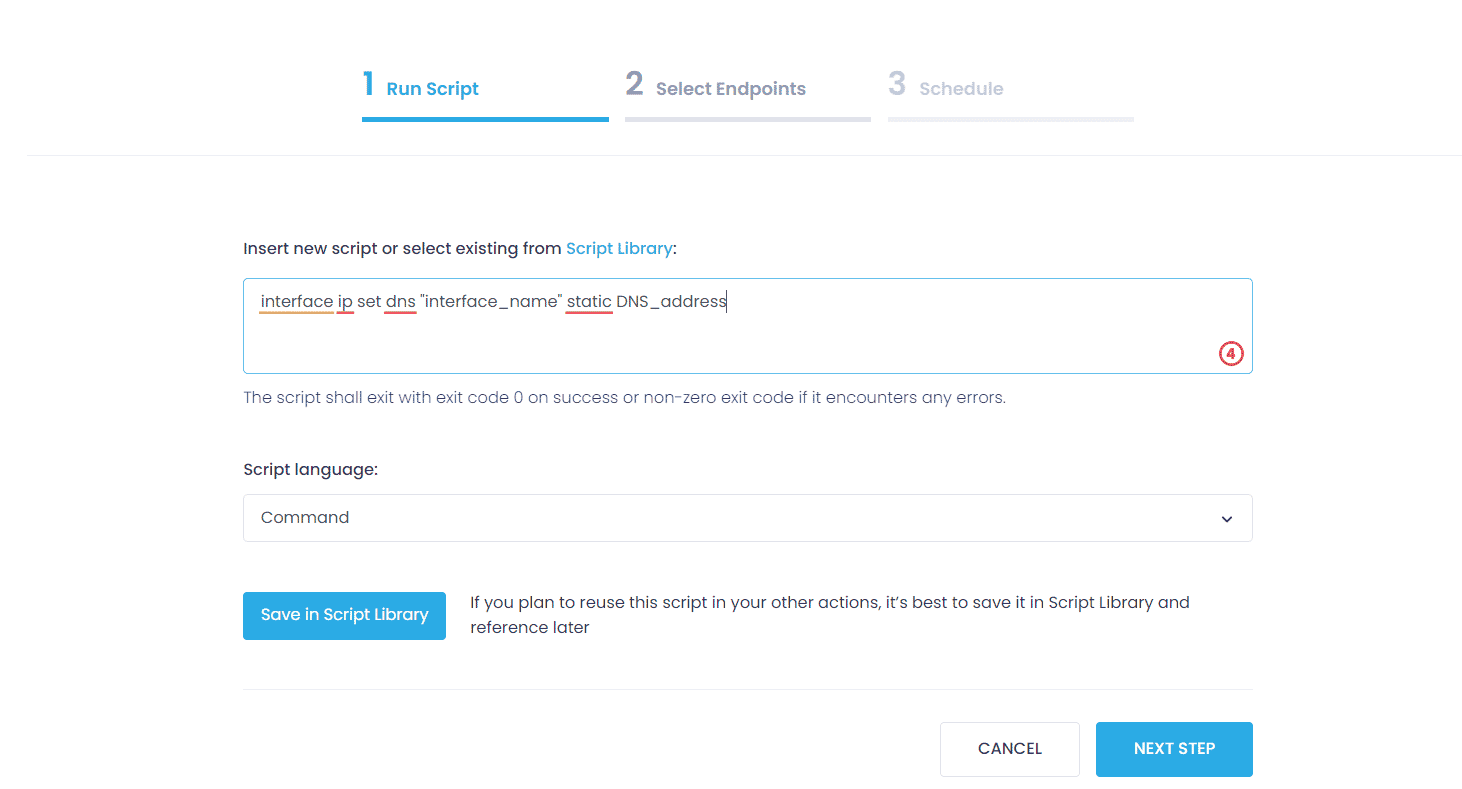
Step 3: Choose Script language and type this command to change DNS:
interface ip set dns "interface_name" static DNS_address
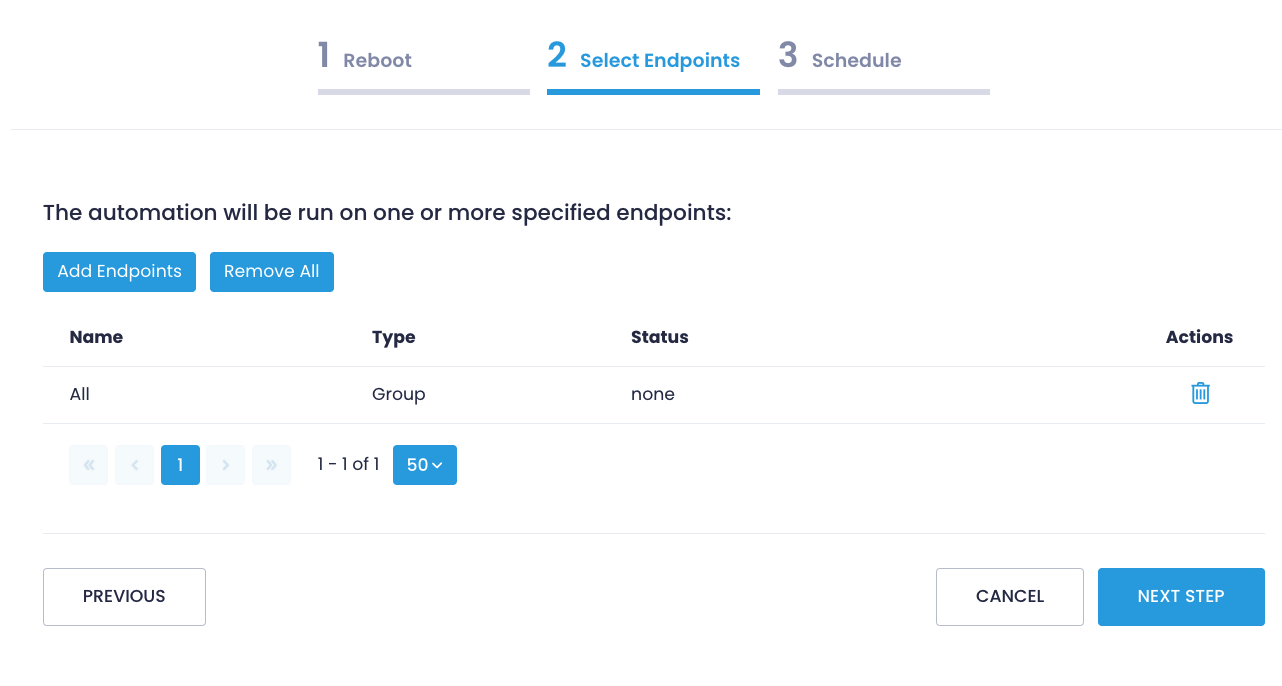
Step 4: In the Select Managed Endpoints window, you mark those endpoints on which you are going to change DNS. You can add all the available endpoints or mark them one by one.
Step 5: Schedule the action (Run now/ No schedule yet/ At specific time/ Repeat) and Finish.