
The recent discovery of CVE-2023-36884 has raised concerns within the cybersecurity community. With no available patch to address the vulnerability as of July 12th, 2023, it becomes crucial to explore mitigation options. In this blog post, we will examine the recommended steps to safeguard your software stack and protect against potential exploits.
Understanding the Vulnerability
Office and Windows HTML Remote Code Execution Vulnerability (CVE-2023-36884) is an important zero-day vulnerability that impacts Office and Windows HTML. It possesses a network attack vector with high complexity, requiring user interaction but not elevated privileges. With a CVSS rating of 8.3, it is categorized as important, although it could potentially warrant an even higher severity if executed with user interaction and complexity. The vulnerability affects all versions of Windows Server from 2008 onwards, Windows 10, as well as Microsoft Word and Microsoft Office versions 2013 and later.
Exploiting this vulnerability entails an attacker creating a specially crafted Microsoft Office document capable of executing remote code in the victim’s context. However, it is important to note that convincing the victim to open the malicious file is a prerequisite for a successful attack.
Depending on the software stack you are running, the CVE-2023-36884 vulnerability may pose a significant risk. As Microsoft points out in their post (available here), customers using Microsoft Defender for Office 365 and Microsoft 365 Apps (Versions 2302 and later) are protected from attachments and exploitation attempts related to CVE-2023-36884.
Considering Microsoft’s confirmation of active exploitation and the lack of an immediate patch, it becomes imperative to implement effective mitigation measures. Additionally, it is essential to prepare your employees to recognize and defend against potential phishing attacks associated with this vulnerability.
Mitigation
For those who do not have the aforementioned software packages in place, an alternative mitigation option is available. However, it’s important to note that while the following registry settings will mitigate the issue, they may impact the normal functionality of certain applications.
Registry Configuration:
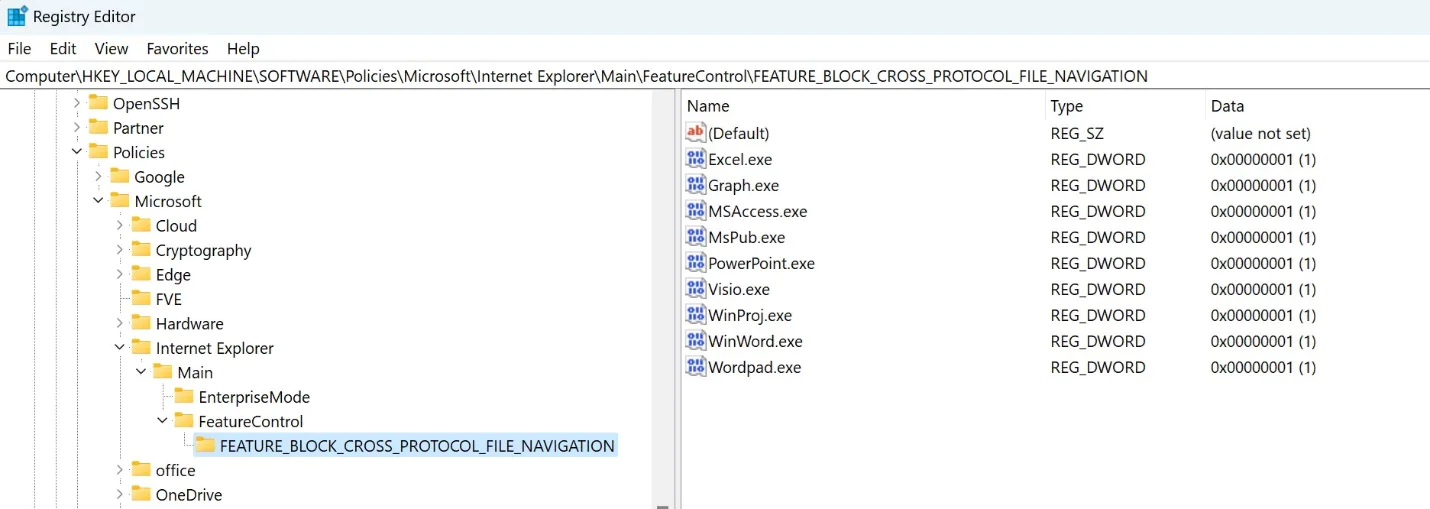
To implement the mitigation, we need to add specific application names to the following registry key:
Registry Key: Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION
Applications to Add:
- Excel.exe
- Graph.exe
- MSAccess.exe
- MSPub.exe
- Powerpnt.exe
- Visio.exe
- WinProj.exe
- WinWord.exe
- Wordpad.exe
Please ensure that each application name is added as a value of type REG_DWORD with a data value of 1.
To simplify the deployment of the registry changes across multiple systems, you can leverage the following PowerShell script. This script can be deployed using Action1 or other deployment methods:
$values = @(
“Excel.exe”
“Graph.exe”
“MSAccess.exe”
“MSPub.exe”
“Powerpnt.exe”
“Visio.exe”
“WinProj.exe”
“WinWord.exe”
“Wordpad.exe”
)
$targetPath = “Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION”
$fbcpfn = Test-Path -Path $targetPath
if (-not $fbcpfn) {
New-Item -Path $targetPath -Force | Out-Null
}
$values | ForEach-Object {
$regValue = Get-ItemProperty -Path $targetPath -Name $_ -ErrorAction SilentlyContinue
if ($regValue) {
try {
Set-ItemProperty -Path $targetPath -Name $_ -Value 1 -Force -ErrorAction Stop | Out-Null
}
catch {
$Host.UI.WriteErrorLine(“Failed to set registry value for $_”)
}
}
else {
try {
New-ItemProperty -Path $targetPath -Name $_ -Value 1 -PropertyType DWord -Force -ErrorAction Stop | Out-Null
}
catch {
$Host.UI.WriteErrorLine(“Failed to set registry value for $_”)
}
}
}




