Action1 arms internal IT departments and MSPs with advanced scripting capabilities to mitigate Follina, a newly discovered Windows zero-day. The service is free for the first 200 endpoints.
An Alarming New Windows 0-Day Vulnerability
A new and very dangerous Microsoft Windows zero-day vulnerability was recently discovered. Tracked as CVE-2022–30190, it is nicknamed “Follina” because the spotted sample references 0438, the area code of Follina, Italy.
Follina was assigned a CVSS score of 7.8 on a scale of 10, but it is a serious threat for several reasons:
- The scale of the threat — Follina affects most Windows machines. It applies to Microsoft Office 2013, 2016, 2019, 2021; Office ProPlus; and Office 365. It also applies to Windows itself, because it can be called from .lnk files.
- The simplicity of exploitation — Follina enables the execution of PowerShell code when a user opens an infected Word document. It works without elevated privileges, does not require macros to be enabled, and bypasses Windows Defender detection. Moreover, if the document is saved in RTF format, the user does not even have to open the file; the malicious payload will be executed via the preview tab in Windows Explorer.
- Wide availability — A proof of concept (POC) is publicly available, so every hacker is able to create an exploit themselves or purchase one on the darknet.
In short, this vulnerability empowers attackers to create sophisticated phishing campaigns that cause recipients to unknowingly launch malware. The potential for damage is huge: Hackers can encrypt, steal or modify data; move laterally through the network; disrupt services; and create backdoors for future exploits. They could even make the affected hosts part of a botnet.
Current Workaround
Microsoft has not yet released a patch to mitigate the vulnerability. Instead, it offers a manual workaround that involves disabling the MSDT URL protocol by modifying the Windows registry as follows:
- Run the command prompt as an administrator.
- Back up the registry key with the command:
reg export HKEY_CLASSES_ROOT\ms-msdt filename - Delete a key using the command:
reg delete HKEY_CLASSES_ROOT\ms-msdt /f
Implementing this workaround can be cumbersome. The script from Microsoft does not check whether you have a key in the registry that needs to be backed up and deleted, nor does it check whether you already have a working backup. Moreover, if you accidentally execute the script more than one time (for example, through human error or due to settings in Group Policy or the task scheduler), then the script can replace a working backup with a non-working one.
In addition, deploying the script manually through Group Policy can be time consuming and labor-intensive. That’s especially a concern if many endpoints are remote, since using VPN to deploy updates via Group Policy is unwieldy: IT teams will have to connect to each device, one after another, and run the script manually. The resulting delay in mitigation puts the organization at serious risk.
Moreover, when the official patch becomes available, IT teams will have to go through the same process to revert the changes from the workaround in order to avoid issues caused by Windows registry key deletion, and then to deploy the patch.
Action1’s Free Automated Scripting Solution
Internal IT teams and managed service providers (MSPs) can leverage Action1 to quickly and efficiently implement Microsoft’s suggested workaround to mitigate this critical vulnerability across their remote and in-office endpoint in bulk — and the tool is free for the first 200 endpoints.
Even better, the Action1 research team has developed a batch file that minimizes risk during script execution — unlike the script from Microsoft, our script performs all necessary checks and asks for confirmation about whether the current backup needs to be overwritten.
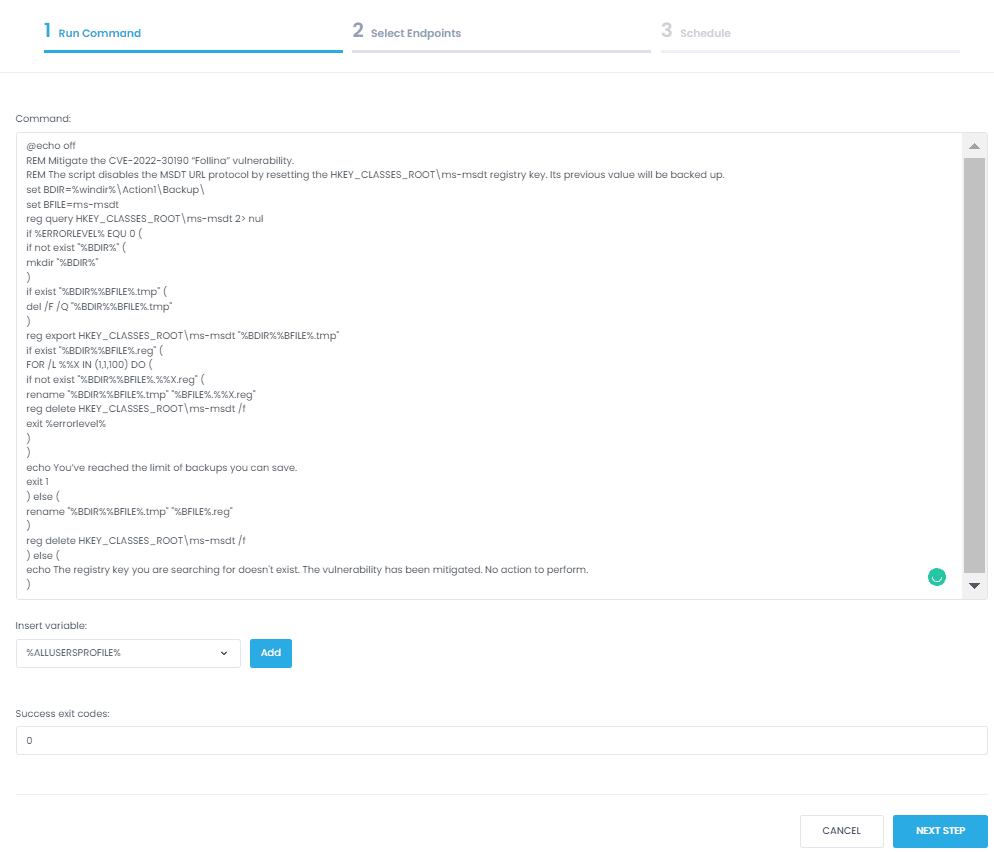
@echo off
REM Mitigate the CVE-2022-30190 “Follina” vulnerability.
REM The script disables the MSDT URL protocol by resetting the HKEY_CLASSES_ROOT\ms-msdt registry key. Its previous value will be backed up.
set BDIR=%windir%\Action1\Backup\
set BFILE=ms-msdt
reg query HKEY_CLASSES_ROOT\ms-msdt 2> nul
if %ERRORLEVEL% EQU 0 (
if not exist "%BDIR%" (
mkdir "%BDIR%"
)
if exist "%BDIR%%BFILE%.tmp" (
del /F /Q "%BDIR%%BFILE%.tmp"
)
reg export HKEY_CLASSES_ROOT\ms-msdt "%BDIR%%BFILE%.tmp"
if exist "%BDIR%%BFILE%.reg" (
FOR /L %%X IN (1,1,100) DO (
if not exist "%BDIR%%BFILE%.%%X.reg" (
rename "%BDIR%%BFILE%.tmp" "%BFILE%.%%X.reg"
reg delete HKEY_CLASSES_ROOT\ms-msdt /f
exit %errorlevel%
)
)
echo You’ve reached the limit of backups you can save.
exit 1
) else (
rename "%BDIR%%BFILE%.tmp" "%BFILE%.reg"
)
reg delete HKEY_CLASSES_ROOT\ms-msdt /f
) else (
echo The registry key you are searching for doesn't exist. The vulnerability has been mitigated. No action to perform.
)
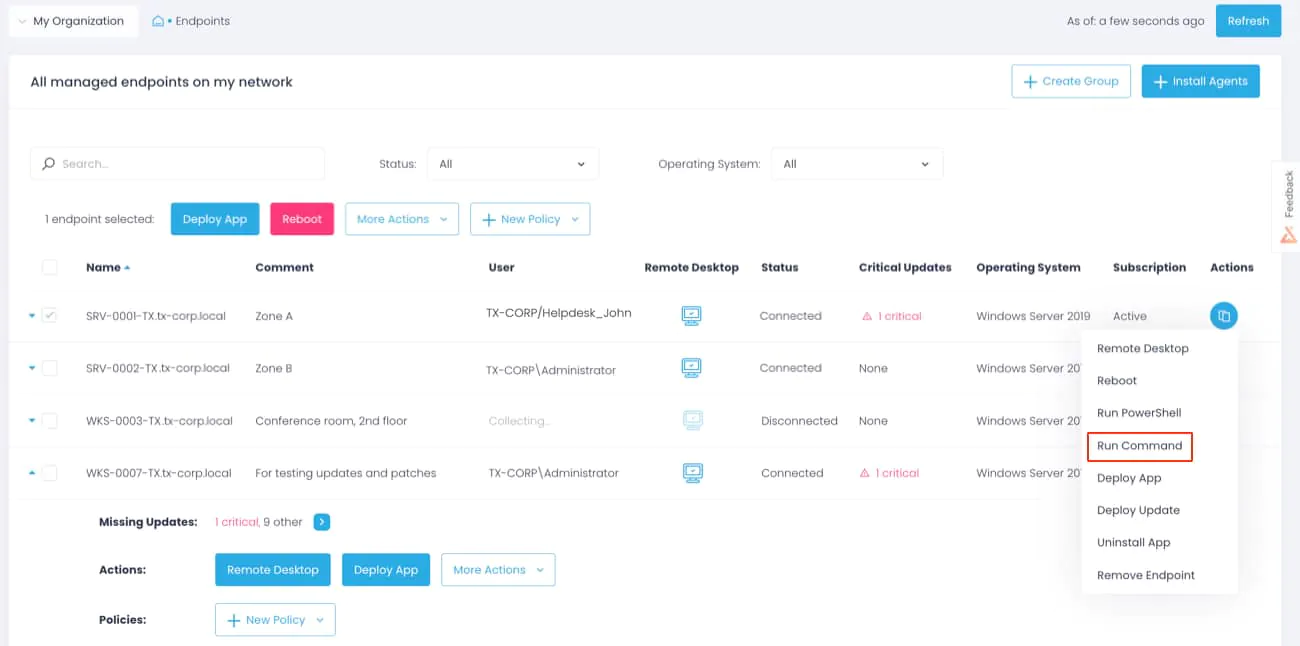
—> Paste in the script provided above:
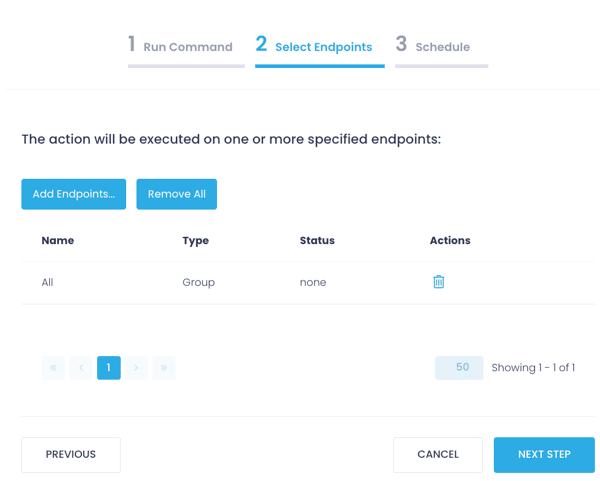
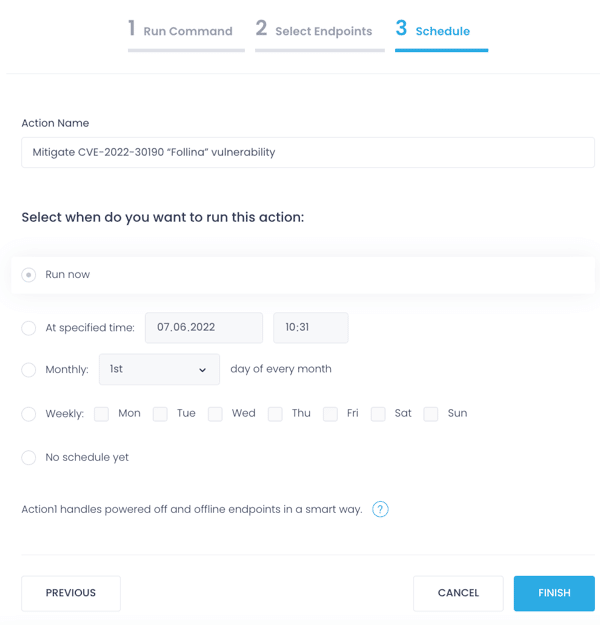
Create Your Free Action1 Account
Protect your organization against “Follina” 0Day vulnerability in a few clicks with the Action1’s powerful scripting and automation capabilities:
PS We are keeping a close eye on the evolving situation around CVE-2022–30190. Once an official patch is available, we’ll facilitate the reversion of the changes to the Windows Registry and deployment of the patch to fix the flaw right away.




