Federal & State Government Patch Management Solution
Unified Cross-OS and Third-Party Patching
No VPN Required – Patch your endpoints from anywhere, anytime.
RBAC – Least privilege, maximum control, secure patching.
Easy Scalability – Limitless growth, zero complexity.
Risk-Based Patching – Automated prioritization, faster remediation.
Unified Cross-OS Patch Management
Manage and update your Windows, macOS, and Linux endpoints directly in your browser from anywhere around the world with no VPN required. Action1’s Autonomous Endpoint Management platform delivers real-time visibility into vulnerabilities, missing patches, and compliance status, enabling your IT team to remediate security gaps with patch management software that just works.
Windows OS
Keep your Windows 10/11 and Windows Server endpoints secure and compliant by automating update/patch deployments and report generation in just a few clicks. Avoid unexpected downtime by remediating vulnerabilities with phased, risk-free, autonomous rollouts.
macOS
Automate patching across your entire macOS fleet. Identify vulnerabilities and missing updates in real time, test patches thoroughly, and schedule seamless deployments to turn manual patching into a set-it-and-forget-it process.
Linux
Keep your Debian and Ubuntu distributions secure and stable with automated updates that never fall behind (Red Hat and SUSE support coming soon). Less downtime, stronger security, no manual overhead—just patching that works.
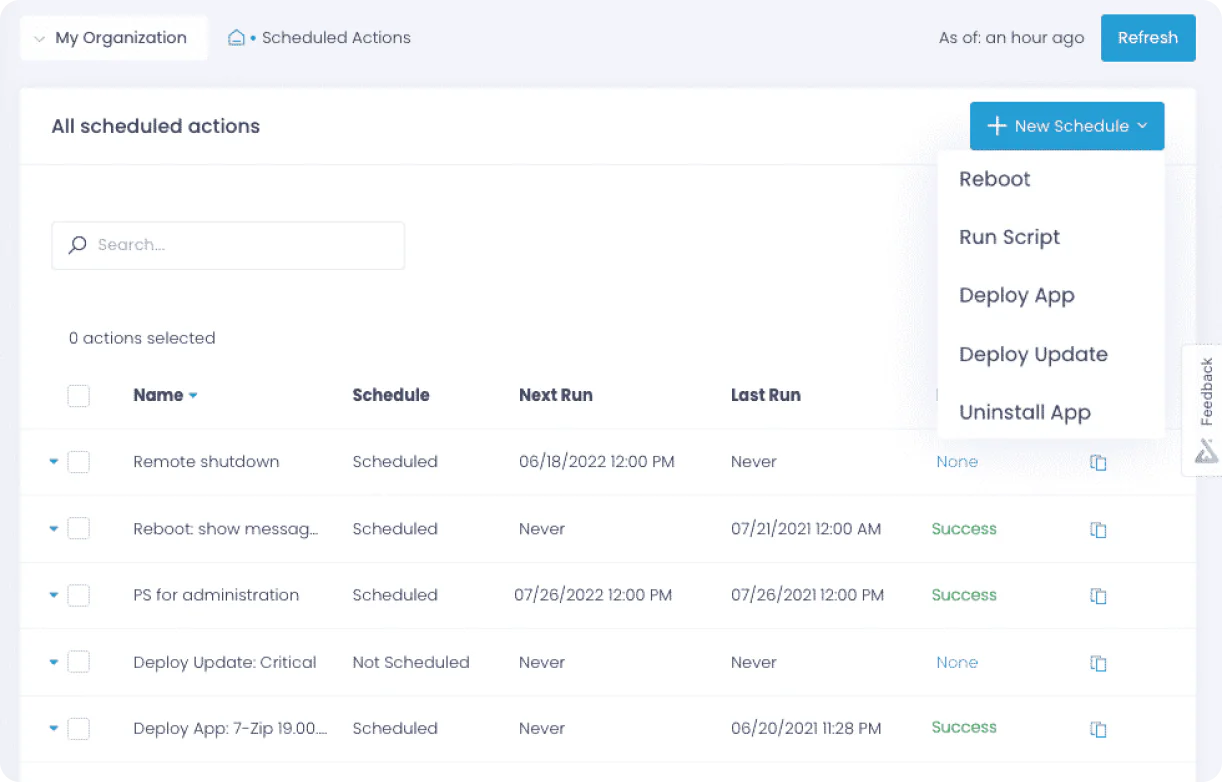
Why Action1 Is Essential for the Government Sector
From compliance to seamless scalability, Action1 helps government agencies secure their endpoints, automate patching, minimize downtime, and meet strict regulatory standards—all with minimal effort.
Compliance & Regulations
Achieve compliance with FISMA, FedRAMP, NIST, ISO 27001, SOC 2 Type II, and HIPAA, along with other regulatory standards through automated vulnerability identification and remediation, detailed audit trails, and real-time compliance reporting. With just a few clicks, track every update, generate customizable reports, and maintain the security documentation government agencies demand.
Role-Based Access Control (RBAC)
Implement fully customizable RBAC with granular permissions that align with government security standards. With Action1, you can define custom roles and assign permissions to specific functions, scopes, or users. This allows you to delegate responsibilities effectively without over-provisioning access, resulting in less risk and a stronger security posture.
Update Rings Deployment
Confidently patch your endpoints through phased, risk-free, autonomous patch rollouts. Updates advance from inner to outer rings based on predefined success metrics, ensuring that only stable patches move forward while problematic ones are automatically stopped. This keeps your endpoints secure and compliant while minimizing downtime.
Easy Scalability
Action1’s cloud-native architecture scales effortlessly from hundreds to hundreds of thousands of endpoints without requiring additional infrastructure or VPN connectivity. The platform works equally well for office-based and remote endpoints, servers, and cloud workloads.
Industry Awards






Trusted by many Fortune 500 companies


Key Features of Action1
Automated Risk-Based Prioritization
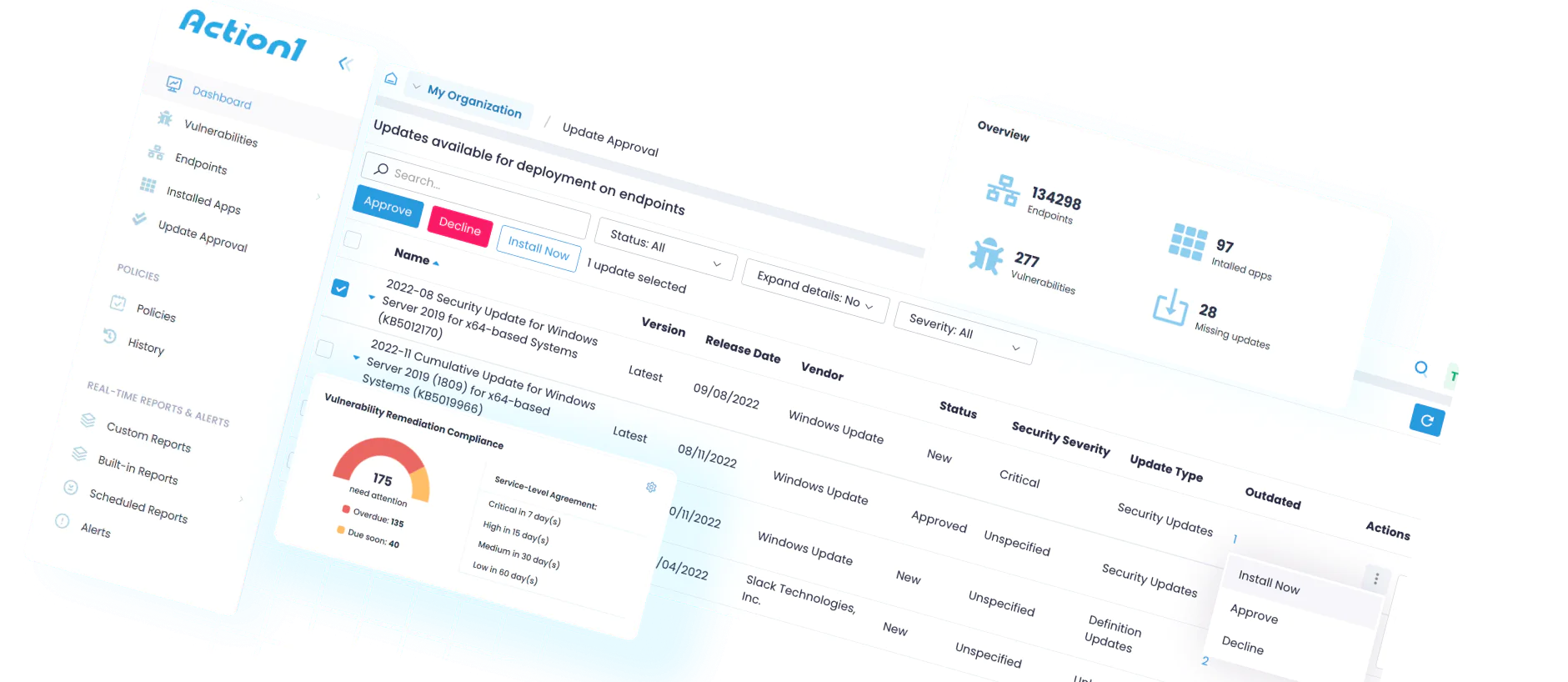
Identify all vulnerabilities in real time across Windows, macOS and third-party applications with automatic prioritization based on CVSS scores, CVE numbers, active exploitation (CISA KEV), and their risk to your organization’s IT infrastructure, ensuring that the most severe threats are addressed first.
Real-Time Reporting & Audits
Get real-time visibility into every endpoint, plus more than 100 built-in customizable reports on patch status, vulnerabilities, security configuration, and software and hardware inventory. Generate audit-ready reports and drill-down insights with just a few clicks.
Offline/Disconnected Endpoint Support
Automatically patch offline endpoints when they reconnect, ensuring no device misses critical updates or continues running outdated software. Deploy patches instantly or on schedule to avoid downtime while keeping every system secure and compliant.
Single Sign-On (SSO)
To provide secure and convenient access, Action1 lets you leverage your existing identity provider for Single Sign-On (SSO), including Entra ID (Azure AD), Okta, Google, or Duo. This eliminates the need to enter user credentials every time you log in.
Peer-to-Peer (P2P) Distribution
Patches and updates are downloaded only once and distributed across your endpoints. This approach minimizes external bandwidth usage and accelerates large software package deployments, all without requiring local appliances or cache servers.
Remote Endpoints - No VPN Required
Manage both your on-premises and remote endpoints from anywhere, directly in your browser with no VPN, appliances, or complex setup required. Action1’s lightweight agents use outbound-only cloud connections to detect missing updates, download, and deploy them securely.
Want to See the Full Feature List?
Download our complete datasheet to explore every Action1 capability, from OS patching to compliance reporting.
Case Studies
What Our Customers Say
A lot of value from Action1 comes from the peace of mind, knowing that your patches are installed, that you are protected from known vulnerabilities which attackers are likely to target with ransomware and other malware.
Action1 saves me 10–15 minutes per machine on software deployment. I can access every device remotely, so I don’t have to literally travel to every location and touch every machine.
Action1 helped us save about 125 hours per month by automating patch management. That’s a huge enabler to our business; as an MSP, the more you automate, the more money you save, and the more savings you can pass on to your customers.
Answers to Your Top Questions
From setup and security to integrations and pricing, here are the answers IT teams look for before choosing Action1.
How can patching be scheduled to minimize disruption across critical government services while still meeting compliance windows?
Patch deployments can be scheduled during off-business hours to avoid operational disruption risks while still meeting compliance windows. Prioritize remediating the most critical vulnerabilities first, then proceed with the rest. Don’t rush rolling out patches before they are tested. Using features like update rings further minimizes downtime risks, because they allow only stable patches that have met success rates to proceed to the outer rings while stopping problematic ones.
How Does a Solution Handle Patching In Air-Gapped or Classified Network Enclaves Typical In Government Infrastructure?
Patch management in air-gapped government networks works through a secure disconnected workflow. First, patches or updates are downloaded, tested, and verified on an internet-connected system. If everything works as expected, these updates are then transferred to the isolated network via cryptographically approved removable media under strict change control. Once uploaded to the air-gapped network, patches are tested again in a lab environment for potential conflicts or compatibility issues. After successful testing, an internal patch server distributes updates across all of the systems. The entire process maintains full audit logging and compliance with NIST 800-53 security controls while preserving complete network isolation.
What Mechanisms Exist for Pilot Testing, Rollback, and Phased Deployment in Government Patch Programs?
Government agencies use a risk-free and staged approach to deploy patches in order to minimize downtime risks. First, they pick a small group of test systems to ensure patches are stable before proceeding to deploy them across all systems. Features like update rings are the perfect fit since you can create multiple rings (groups of endpoints) and set specific success metrics to control whether a patch should progress to the next ring or not. After successful pilot testing, patches automatically roll out in phases, starting with less critical systems and then gradually expanding to more important ones. If a patch causes an operational disruption, many patch management platforms offer a rollback feature that reverts the system(s) to a state before the patch deployment to instantly repair the problem. This phased approach is highly effective at identifying and fixing issues with minimal downtime risks while keeping their networks secure, compliant, and operational.
How Do Role-Based Access, Separation of Duties, and Audit Logging Support Accountability and Oversight In Public Sector Patching?
Using role-based access control, separation of duties, and audit logging ensures that employees have the right permissions, understand their specific tasks, and that everything done during the patching process is recorded.
Role-based access control ensures users only get the permissions they need for completing a specific job. For example, some can manage the entire process, while others can only review or create audit-ready reports. Separation of duties prevents errors, unauthorized changes, and accidental system disruptions. Meanwhile, audit logging records every action, like who deployed a specific patch, when it was deployed, and on which systems. This is of utmost importance, since these logs help investigators trace problems back to specific people and actions, ensuring everyone stays accountable.
These three mechanisms deliver the transparency, security controls, and accountability frameworks that government agencies require for regulatory compliance and risk management.
How Can a Patch Management System Scale Across Multiple Departments, Agencies, or State Jurisdictions While Maintaining Oversight?
Government agencies can share one patch management platform through multi-tenancy while maintaining strict data separation between departments. For instance, Action1 allows you to create separate organizations for different departments or agencies, each with their own endpoints, data, settings, and users. With role-based access control, you can define granular permission levels—ensuring each employee gets exactly what they need within their specific organization. Some users manage the entire process, others only review reports, and some create audit-ready documentation. At the top level, leadership can still monitor everything, check patch and compliance status across systems, and ensure all departments follow the same security strategy. Growth is simple, too, allowing you to scale from hundreds to hundreds of thousands of endpoints without requiring additional infrastructure investments.








