In the pursuit of automation and speed, enterprise IT operations increasingly rely on tools like Chocolatey and WinGet to deploy and manage software at scale. These package managers streamline installation workflows and reduce administrative overhead. But for IT leaders, convenience should never outpace control. Remember, threat actors are counting on your haste, rash decisions, and that the resources you have to stop them, are outgunned by their skills and tools.
Beneath the outward simplicity of these tools, lies a persistent and underacknowledged risk: the structural insecurity of community-maintained repositories. These platforms can, and often do, serve outdated, unpatched, or poorly verified software packages. The consequences of this reality for large organizations are not theoretical. They represent a genuine and growing software supply chain risk.
Outdated Software at Scale
According to Repology’s Chocolatey index and Repology’s Winget index, nearly half of all packages in both Chocolatey and Winget lag behind their latest upstream versions. In many cases, these outdated versions include known CVEs, many of which are actively exploited in the wild. For example, older versions of popular tools like 7-Zip, VLC, and even open-source developer utilities have carried unpatched remote code execution (RCE) and privilege escalation flaws for months before being updated or replaced.
When such packages are deployed across dozens, hundreds, or thousands of machines in an enterprise environment, each installation becomes a potential attack surface. Attackers do not need zero-days when N-day vulnerabilities are quietly delivered by trusted automation pipelines.
Editor’s note: At the time of this writing Repology supported Winget, they have since removed it, so the Winget link now takes you to the archived version of that data so it can still be reviewed. As well Chocolatey’s repo is experiencing usability issues that may subsequently lead to its removal as well, if that happens, we will edit that link accordingly.
Read Also:
So, is this isolated FUD (Fear Uncertainty & Disbelief) promoting alternatives? Really it is not, this applies to these repos compared to ANY product because the deficiency is in the repo itself, this is not suggested “Use this over that” as much as “If you choose to use this, know the facts”. Let’s have a look at the real numbers, where we can see this is not opinion, it is documented verifiable fact.
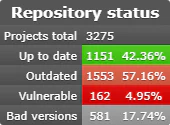
Using chocolatey as an example, you see that as of the time of this writing, there are 3275 active projects, of that 1151 being up to date, 1553 of which are outdated, and even known 162 vulnerable. That is an astounding 57% all the packages in chocolatey at this time are considered outdated and almost 5% KNOWN VULNERABLE.
Notice further that the closer you get to “Now” the worse this problem gets. This is not bleeding edge updates, it is hemorrhaging security on life support.
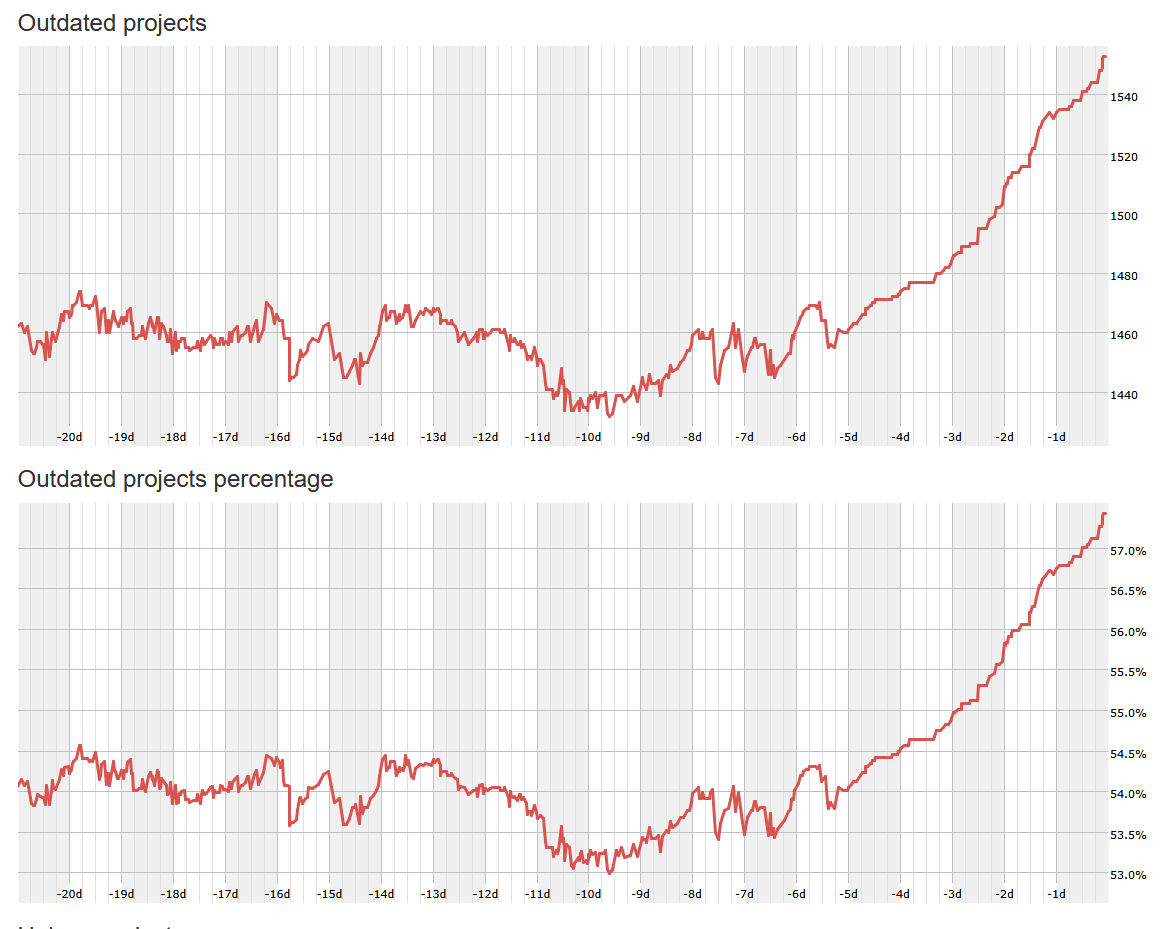
So when an attacker finds out your primary update mechanism is chocolatey (May be implied by RMM choice, or other factors) and they know what software you use, they have basically a barometer to how far behind your business likely is at this time as it relates to vulnerability in your systems.
https://repology.org/repository/winget/problems
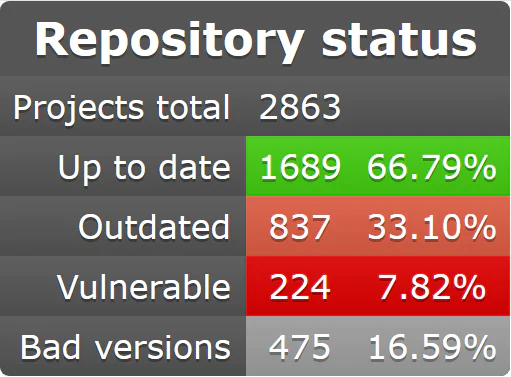
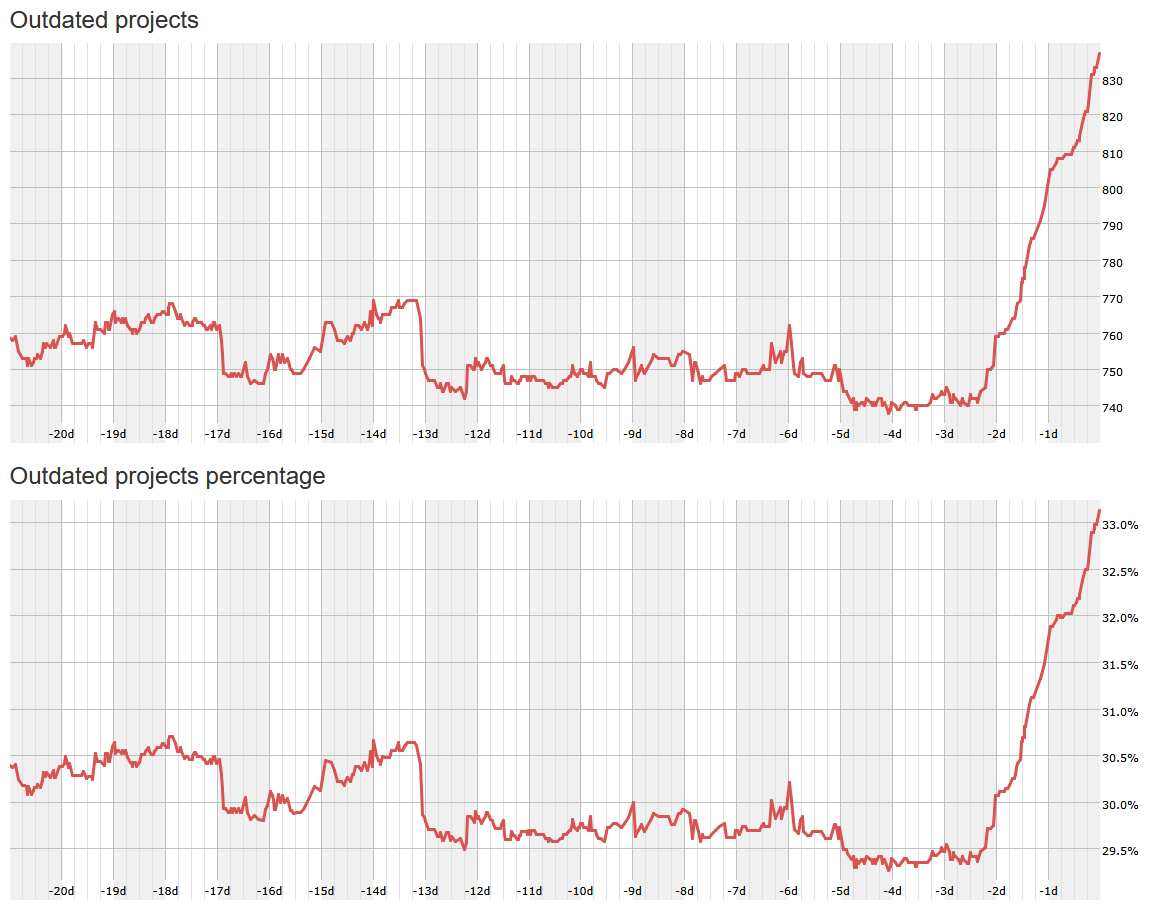
Patching with the wrong or outdated patches can actually end up being a shorter path to compromise. Along with that, “Patching” regularly just creates a false sense of security, was it done, sure, but was it done correctly and up to the minute latest code, not likely.
A Realistic Threat Model: Supply Chain Intrusion
Community repositories open several doors for software supply chain compromise:
- Inactive package maintainers: When a maintainer abandons a package, it remains available in the repository, sometimes for years. If an attacker claims the namespace or masquerades as the original maintainer, they can publish a “harmless” update that introduces malicious behavior.
- Remote installer patterns: Chocolatey in particular allows packages to download binaries from external URLs at runtime. If a developer hosts their installer on GitHub or an unsecured CDN and that source is compromised, malicious payloads can be served directly to unsuspecting endpoints.
- Insufficient update velocity: Even in the WinGet ecosystem, backed by Microsoft and more tightly controlled, many packages are behind their upstream versions. The validation process, while robust, does not guarantee rapid response to upstream security events.
These aren’t just hypotheticals. The 2020 SolarWinds breach demonstrated how attackers can weaponize trusted software update channels to infiltrate high-value targets. While Chocolatey and WinGet were not involved in that attack, the same principles apply. A single compromised package or outdated dependency can give adversaries a foothold in otherwise well-defended environments.
Trust, But Verify, Or Better yet, Avoid
The governance models of these repositories assume that package maintainers are both technically competent and consistently available. But in the real world, developers move on, project interest wanes, and packages rot in place. Even Microsoft’s own repository for WinGet relies on maintainers submitting updated manifests; this introduces a lag between upstream patching and ecosystem-wide propagation.
In high-security environments, finance, healthcare, energy, defense, this is an unacceptable exposure. Just as enterprises vet third-party vendors for compliance, security, and support SLAs, so too should they scrutinize the origins and currency of their software distribution channels.
Recommendations for Enterprise Use
- Avoid community repositories in production environments. Use internal mirrors of trusted software, validated through corporate CI/CD pipelines. Or use trusted vendors that are doing validation and testing for you.
- Treat community-maintained packages as untrusted code. Apply the same sandboxing, inspection, and behavior monitoring you would for downloaded binaries.
- Monitor for package drift. Establish policies to detect when installed software versions lag behind their upstream equivalents and automate alerts.
- Push vendors to support secure delivery via validated enterprise channels. If a tool is essential, lobby for MSI/EXE distribution with signatures, clear update policies, and version pinning.
- Maintain your own packages. Use a patch management system that allows for creation and maintaining packages essential to your business, and only binary’s obtained directly from the vendors. This reduces the number of hands the package passes through and provides a verifiable chain of control.
While package managers like Chocolatey and WinGet can offer value in the right context, but seldom is enterprise that context. For enterprise leaders, the apparent ease of deploying software via community repositories masks a complex web of maintenance gaps, verification blind spots, and update latency. As attackers increasingly exploit trusted channels to infiltrate networks, it is essential to rethink what “trusted” really means.
The risk is not in the tools themselves, but in how much trust we place in an ecosystem that was never designed with enterprise-grade assurances in mind. Security is not convenient, convenience is not secure, make sure not to trade one for the other.





