With security landscapes shifting like the surface of the ocean nowadays, IT and security teams are constantly looking for smarter ways to manage endpoint alerts without being buried under a mountain of notifications. Real-time visibility into security events is crucial, but so is the ability to act on that visibility efficiently.
That’s where the Action1 connector for Zapier becomes a useful interface to extent what is already a powerful system. By combining Action1’s robust endpoint security and patch management capabilities with the automation power of Zapier, organizations can create streamlined, actionable workflows that surface critical alerts in real time across the tools teams already use.
Why Connect Action1 with Zapier?
Action1 is well known for its cloud-native approach to endpoint management, offering continuous monitoring, vulnerability remediation, and compliance reporting across distributed environments. Alerts generated within Action1 often contain key insights, such as unauthorized software installations, missed patches, or security misconfigurations, that require timely review and action.
Zapier acts as the bridge between these alerts and the tools where stakeholders actually spend most of their time daily: Slack, Microsoft Teams, email platforms, ticketing systems like Jira or ServiceNow, or even simple spreadsheets and databases. This connection doesn’t just improve visibility, it enables teams to orchestrate responses, assign tasks, and document incidents, all without adding friction to their workflow.
A Smarter Way to Handle Alerts
Using the Action1 connector on Zapier allows you to selectively route alerts based on relevance or severity. Instead of receiving every alert into a generic channel or inbox, you can tailor automations to match your organizational context. For example:
- Critical security alerts can be pushed directly into a high-priority Slack channel or opened as incident tickets in Jira.
- Compliance-related alerts can be logged into Google Sheets for audit tracking.
- Maintenance-related alerts, such as systems missing updates, can trigger reminders in Microsoft Teams or send emails to local IT admins.
This level of customization prevents alert fatigue and ensures that the right people see the right information at the right time.
Enhancing Collaboration and Accountability
Another benefit of integrating Action1 with Zapier is how it supports cross-functional collaboration. Security teams can raise issues in real time to IT operations, legal, or compliance, depending on the nature of the alert. By automatically generating tickets, tasks, or notifications in the preferred platform of each team, organizations reduce the time between detection and resolution.
Even better, automation through Zapier leaves behind a digital audit trail. Alerts don’t disappear into the void. Each one can be archived, tagged, and tracked, contributing to a broader security intelligence framework.
Reducing Manual Overhead
Teams should not have to manually monitor consoles, export logs, and update ticketing systems by hand. This not only consumes valuable time but introduced the potential for human error or oversight. With the Action1-Zapier combo, you can automate routine parts of the alerting process and free up your team to focus on deeper analysis and decision-making. In many cases, this automation can also help meet SLAs and compliance requirements more consistently by ensuring that nothing falls through the cracks.
Final Thoughts
Using the Action1 connector for Zapier isn’t just about pushing alerts from one place to another. It’s about building a proactive alerting ecosystem that enhances visibility, accountability, and responsiveness across your organization. It puts critical endpoint security data in motion, where it can actually drive action.
Whether you’re scaling your IT operations or tightening your cybersecurity posture, the integration offers a lightweight but powerful way to stay ahead of issues without getting lost in the noise.
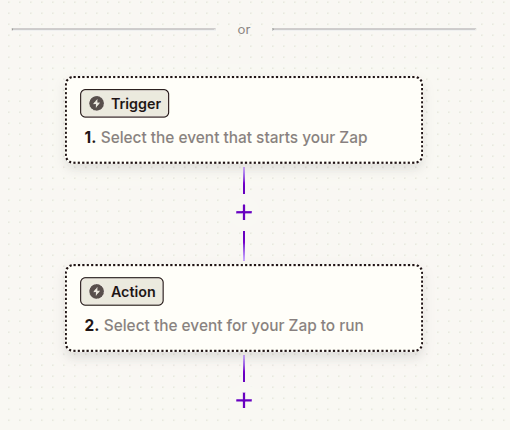
Let’s build something! To get started, if you have not already, create a Zapier account, and then a set of API credentials in Aciton1. Once in Zapier, chose to create a new Zap.
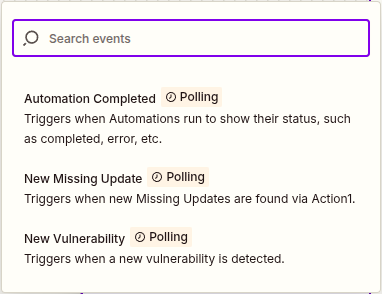
Choose “Trigger” and search for / add the Action1 connector.
Choose an event for “Trigger Event: in this case, we will use ‘Automation Completed’
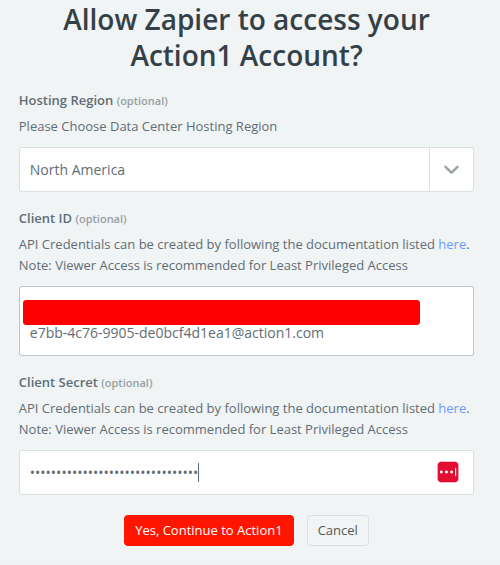
Then choose “Account” and enter the API credentials and region.
Choose “Yes, continue to Action1”, After is connected, choose “Continue”
Enter your ORG ID, then continue, and finally “Test Trigger”
Select a record from the test query and
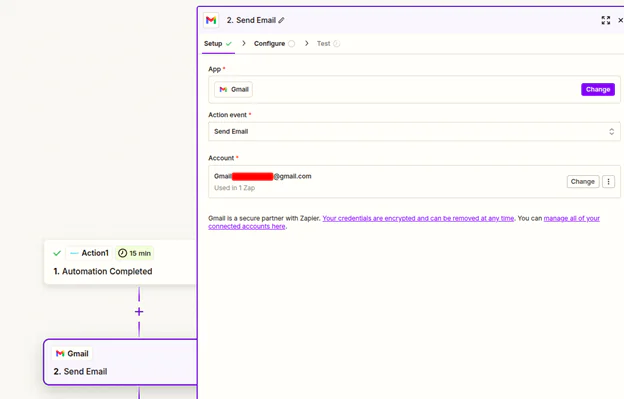
And then ‘Continue with the selected record.’, you will then be prompted to select a service to send that alert to when a new record is detected. For the sake fo demonstration, I chose Gmail, configured for my account, and ‘Send Mail’
In the next step, fill out message details, field mapping from the alert to the email, and other details to your liking, then test. That’s it! You are now setup to receive alerts on the success / failure of your automations.
You can create as complex or simple a workflow and alerting process as your heart’s desire, Zapier supports a large library of connectors.
About Action1
Action1 is an autonomous endpoint management platform trusted by many Fortune 500 companies. Cloud-native, infinitely scalable, highly secure, and configurable in 5 minutes—it just works and is always free for the first 200 endpoints, with no functional limits. By pioneering autonomous OS and third-party patching with peer-to-peer patch distribution and real-time vulnerability assessment without needing a VPN, it eliminates routine labor, preempts ransomware and security risks, and protects the digital employee experience.
In 2025, Action1 was recognized by Inc. 5000 as the fastest-growing private software company in America. The company is founder-led by Alex Vovk and Mike Walters, American entrepreneurs who previously founded Netwrix, a multi-billion-dollar cybersecurity company.