Microsoft’s WinRE update poses challenges for PCs with small partitions, causing “Windows Recovery Environment servicing failed” error. Solutions fprovided.


Microsoft’s WinRE update poses challenges for PCs with small partitions, causing “Windows Recovery Environment servicing failed” error. Solutions fprovided.

January 2024 Patch Tuesday updates, vulnerabilities found in third-party applications.

As we wave goodbye to 2023, let’s explore what the cybersecurity future holds for us in 2024 and beyond.

December 2023 Patch Tuesday updates, vulnerabilities found in Microsoft Access and third-party applications.

A key development in cybersecurity is the release of CVSS version 4.0 by FIRST, marking a major advancement since CVSS v3.0’s introduction over a decade ago.

This blog post explores how the new release of Action1 delivers tangible benefits, enhancing cybersecurity and operational efficiency in your organization

How AI can add value to patch management helping you navigate the realm of AI in enterprise tech and cybersecurity more effectively.

November 2023 Patch Tuesday updates and vulnerabilities found in third-party applications
Discover how to seamlessly configure single sign-on with Microsoft Entra ID Azure AD in Action1. Streamline access management for your organization.

Action1 has been named a Momentum Leader in patch management and has earned 81 badges by G2, the world’s largest and most trusted software marketplace.

October 2023 Patch Tuesday updates and vulnerabilities found third-party applications

Recent security disclosures unveiled a critical vulnerability in ‘libwebp’ library. Action1 aids in promptly detecting vulnerable software

September 2023 Patch Tuesday updates and vulnerabilities found in third-party applications.
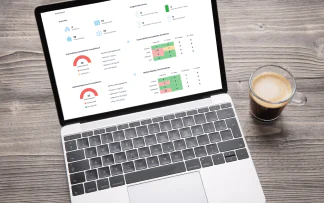
The updated Action1 platform brings together vulnerability discovery and remediation and here’s why we’re absolutely excited about these capabilities!

Reflecting on the Equifax breach: its impact on 147M people, lessons learned, and Equifax’s Security Controls Framework.

Exploring the existential threat of ransomware using the Illinois Hospital closure as a case study.

Exploring Verizon’s DBIR 2023 insights on defending against stolen credentials, phishing, and vulnerability exploitations.

August 2023 Patch Tuesday updates, and vulnerabilities found third-party applications.

Action1 is acclaimed as effective security software, earning 2023 Best Value and Ease of Use Badges from Capterra reviewers.

CISA’s #StopRansomware Guide: why regular patching and effective vulnerability management are crucial in your strategy against escalating ransomware threats