Action1 Endpoint Management:
Cloud-Native, Secure, Easy-to-Use
Manage work-from-anywhere enterprises without weeks of training
Cloud-native patching, deployment, monitoring, and remote access
Modern, refined, lightweight: not bloated with features
Dozens of pre-built apps, scripts, reports, and alerts
Secure and trusted: SOC 2 Type II and ISO 27001:2022
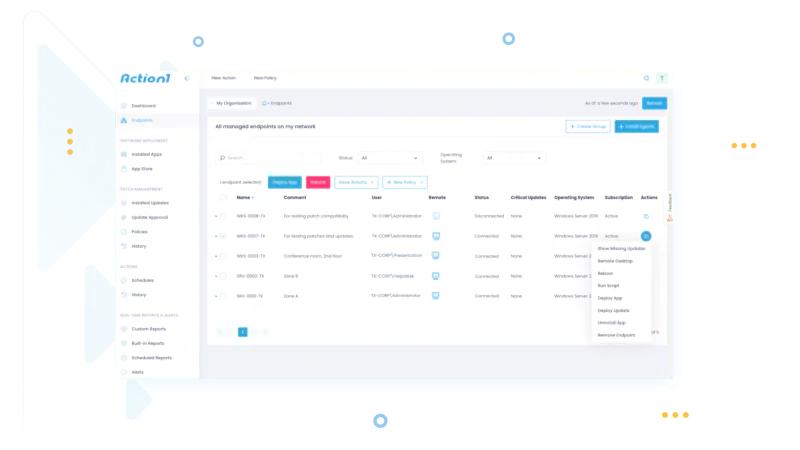
Endpoint management without weeks of training
Schedule automated remote management tasks. Patch endpoints and deploy software without bandwidth issues. Gather IT asset inventory, software, and hardware info in real time. Proactively monitor multiple endpoints simultaneously. Provide remote support via a built-in remote access tool.
IT automation
Remotely run PowerShell and CMD scripts across multiple computers. Pick from the library of pre-built scripts or add your custom ones for further use.
Real-time reports and alerts
Monitor and manage endpoints with on-demand and scheduled reports and alerts. Pick from predefined reports or build virtually any custom one.
IT asset inventory
Get a real-time inventory of your hardware and software assets to make more informed decisions on your endpoint management efforts.
OS and application patching
Update both OS and third-party applications from a single console consistently across all your endpoints.
Software deployment
Deploy and remove applications ad-hoc or at scale. Choose apps from the built-in App Store or add your custom apps.
Remote access
Support users and maintain servers directly from your web browser without any additional software, RDP and VPN.
Industry Awards






Trusted by thousands of IT teams around the world
10M+
Managed Endpoints
99%
Patching Success
1 hour
to configure


Why customers choose Action1
Break free from VPN
Update and manage remote and onsite endpoints with Action1 Platform. No company network, domain, or VPN required.
Configure in 1 hour
Start getting value from day one with a solution that is easy to deploy and just works. No legacy technology and feature overload.
Phenomenal ROI
No additional hardware or software to deploy. Get your first 100 endpoints free, with no strings attached. Scale up as needed at a flat per-endpoint price.
Reach offline devices
Automatically catch up on updates, software deployment, script execution, and other tasks missed as soon as endpoints get back online.
Optimize distribution
Deliver software and updates faster without burdening your network by relying on your own endpoints to distribute packages.
Get support you deserve
If any issues with our platform arise, have them promptly and definitively resolved by our knowledgeable and responsive support.
What Our Customers Say
Action1 empowers us to increase operational efficiency dramatically by streamlining our remote IT management. The elements we love most in Action1 are the power of scripting, the ability to add or remove software remotely, and the software inventory reporting.
Thanks to Action1, we save two work weeks per year at a minimum, and we are probably underestimating the time savings. In addition, we avoid the expense of having to replace machines because now we can keep careful track of all our IT assets.







